
Senior Design Projects
A requirement for graduation, undergraduate student teams take on year-long capstone projects, putting their problem-solving skills to the test and collaborating to take an idea from concept to design to prototype. On the fourth Thursday in May, teams present their work to an audience of industry experts, faculty advisors, students, family, and friends of the School of Engineering at the annual Senior Design Conference—a highlight of our academic year.
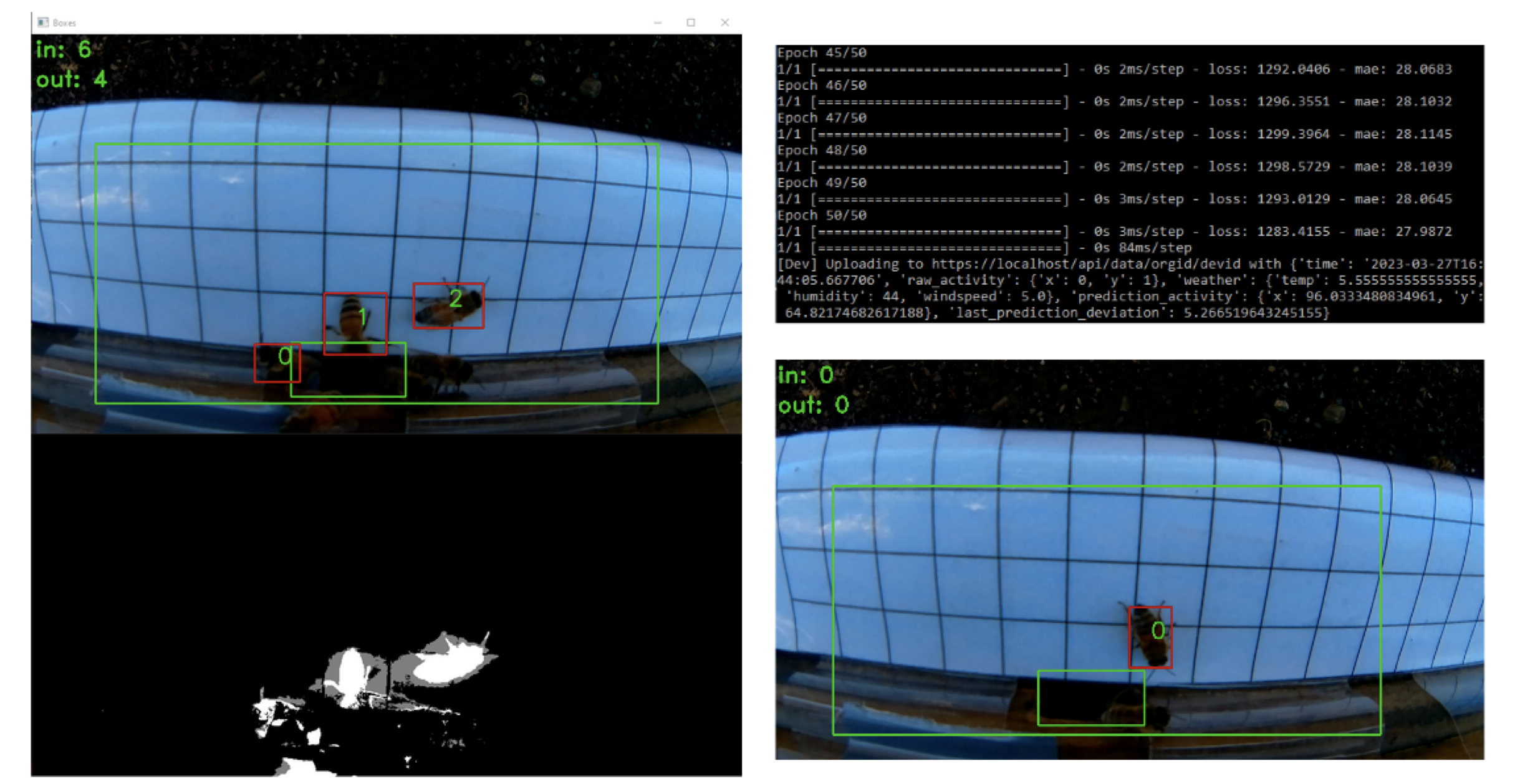
A Study of Processing Beehive Monitoring Data in Edge and Cloud
Cheng Zhang, Jason Fong, Yen-Jung Lu, Niyitanga Inosa, Chan Nam Tie
Bees are vital pollinators for numerous crops and plants, playing an essential role in maintaining the world’s ecosystem and food security. Without bees, the global food supply would be threatened, potentially leading to food shortages and increased food prices. Current beehive monitoring solutions in the market are often prohibitively ex- pensive, some commercial beehive monitoring solutions can cost upwards of thousands of dollars. This makes them inaccessible to many small-scale beekeepers. To help protect bee health and ensure the survival of thousands of plant species worldwide, this project aims to create an accessible solution for individuals to monitor the health and activity of bee hives. The solution would use cheap and accessible tools to capture the activity of the bees, analyze it with local weather data, and alert the user when the actual activity is significantly different from the prediction, thus allowing beekeepers to more effectively tend to their many hives around the world.
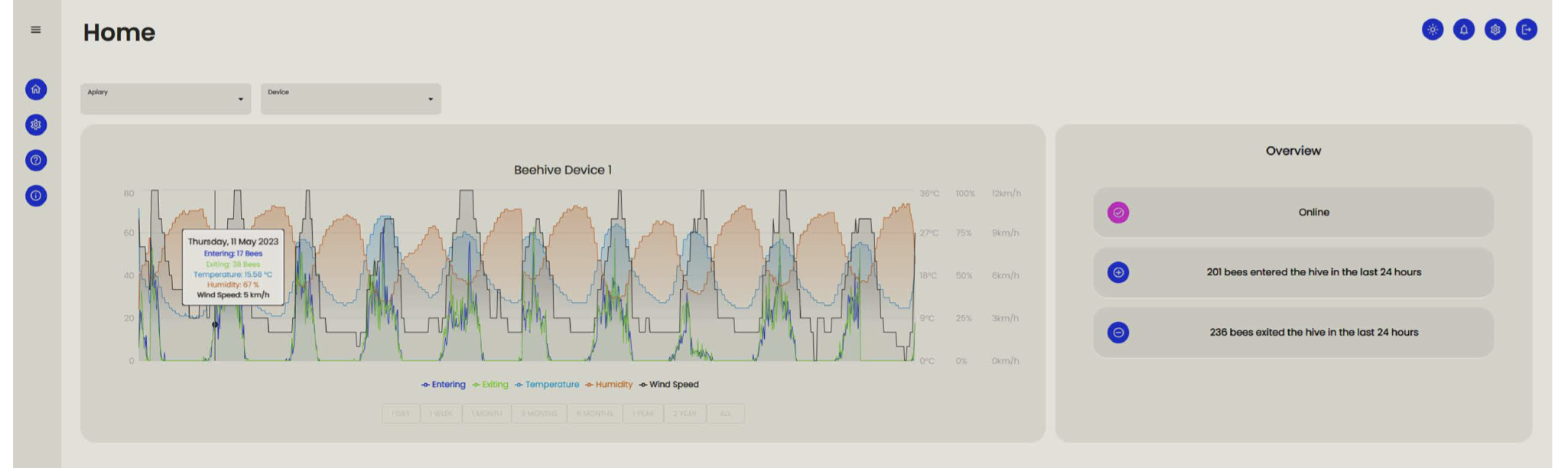
A Hardware Platform for Wireless Beehive Monitoring
Erik Wrysinski, Collin Paiz, Jonathan Stock, Daniel Blanc
Beehive monitoring is currently a novelty. These monitoring devices are expensive to set up, difficult to implement, and lack cross compatibility with each other. Preexisting beehive monitoring solutions face all of these shortcomings. Our beehive monitoring platform aims to overcome these issues by using inexpensive, off-the-shelf, open-source hardware paired with a computer vision machine learning model to accurately monitor the ingress and egress of bees into and out of the hive. This data is presented to the beekeeper in a simple GUI which allows them to track hive activity over time, and by extension, the overall health of the hive.
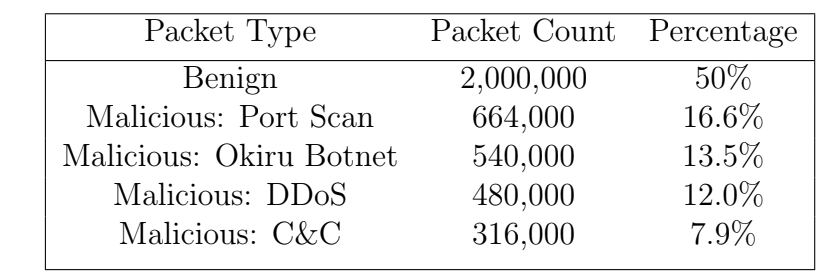
AI-Powered IoT Monitoring and Security for Smart Homes
Timothy Hradil, Pavel Boldyrev, Matthew Ding
Smart home devices are becoming increasingly popular across the United States. Unfortunately, in order to keep the cost of these devices down, manufacturers tend to place cybersecurity measures lower on their list of priorities. As a result, these devices have become targets for security breaches like the Mirai Botnet and distributed denial of service (DDoS) attacks. The cybersecurity solutions currently available on the market are either expensive, difficult to set up, or follow a static set of rules for attack detection. In this thesis, we propose a novel approach to detecting attacks on Internet of Things (IoT) devices through the use of a forward proxy powered by a machine learning model running on a Raspberry Pi. Our proposed solution is more affordable, requires minimal configuration, and dynamically adjusts detection rules based on prior attacks. The use of a machine learning model in the solution allows us to take advantage of the regularity in IoT traffic patterns to identify and isolate potentially malicious packets. Our model was trained using the IoT-23 data set, which provides a labeled set of malicious and benign packets from IoT devices. We verified the effectiveness of our approach using a testbed of various smart home devices set up in an isolated home network. These devices range in price and usage context, allowing us to ensure that our solution will be effective with the majority of smart home devices. After testing, we have determined that our model is able to successfully identify and isolate XX% of malicious packets sent from a compromised IoT device. Moving forward, we hope to implement our solution directly onto the router hardware using the P4 language for widespread adoption.
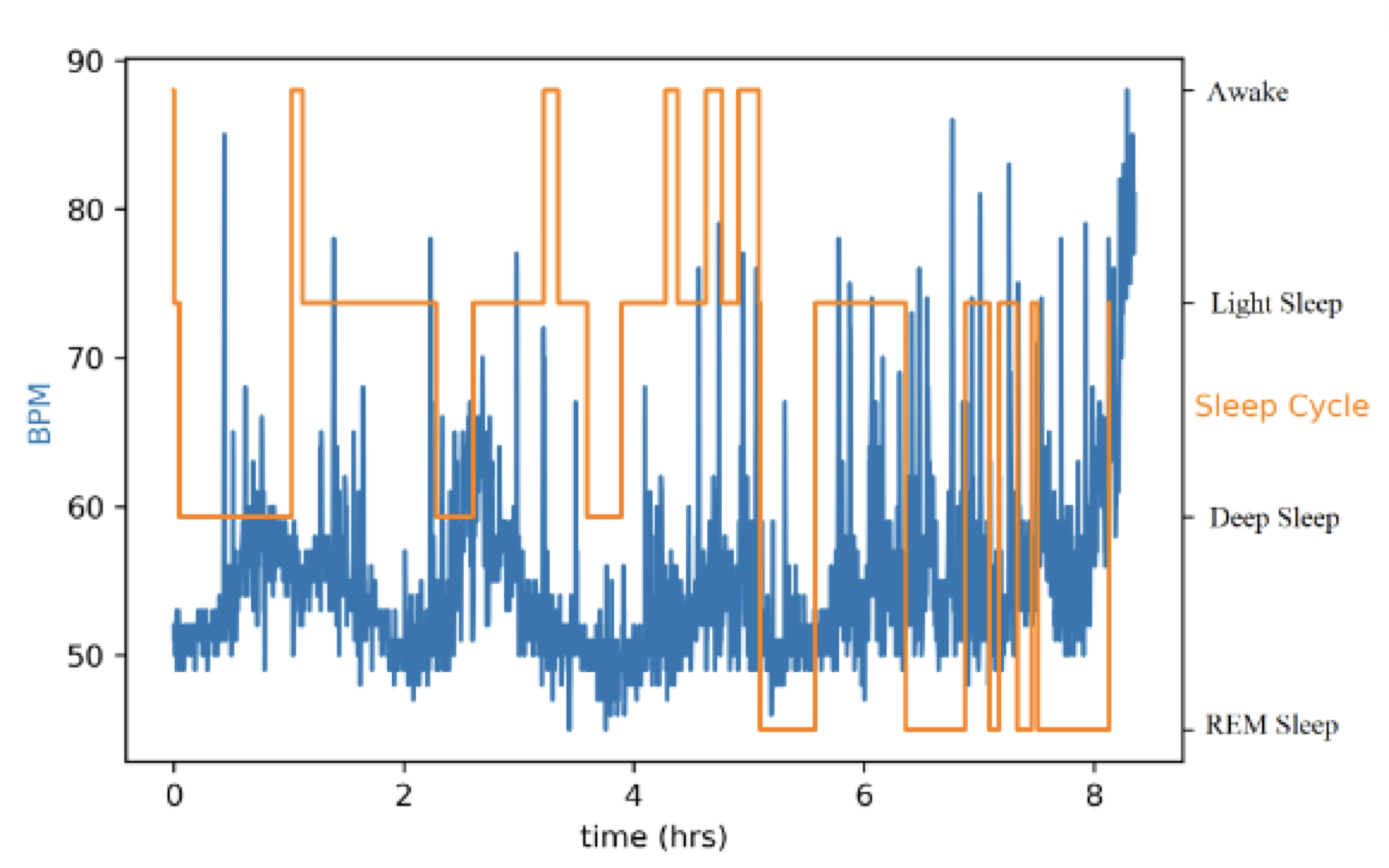
DreamTemp: Sleep Monitoring and Improvement System
Kyle Pedersen, Michelle Lim, Will Cockrum
An interesting consideration is that for complex ML models, at some point the overhead from using eBPF’s special data structures becomes larger than the benefit that eBPF confers. For example, interesting future work would be to test whether random forests (RFs) or deep NNs can also achieve a performance advantage when implemented in eBPF. In this work, however, we could show that for a simple decision tree model, eBPF provides a significant performance advantage. With 70 million Americans suffering from chronic sleep disorders and only 7500 board-certified sleep physicians, a clear logistical problem exists that technological solutions may be able to address. The proliferation of IoT devices in homes and on our person presents a unique opportunity to improve sleep quality by leverag- ing the data they produce, and the control they provide to us over our everyday lives. DreamTemp is a platform for sleep monitoring and improvement that aims to improve an individual’s quality of sleep by dynamically adjusting the room tempera- ture based on the user’s sleep cycle using a smart wearable and thermostat. Through future studies that will investigate the effectiveness of our system in improving sleep quality, we hope to improve the health and quality of life of the population.
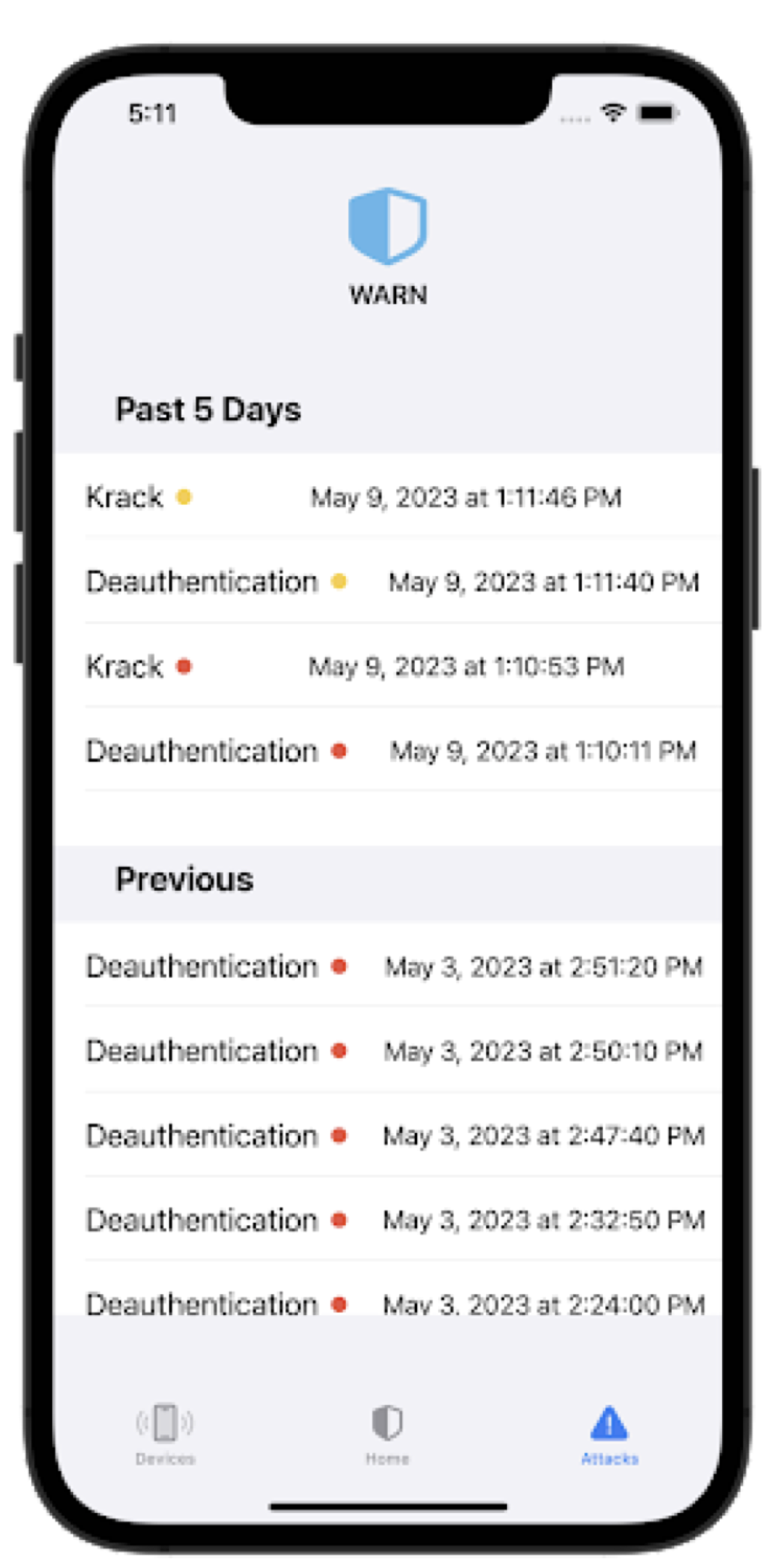
W.A.R.N (WI-FI Attack Recognizer and Notifier
Sudhish Sewpaul, Tate Musante, Jaden Ngo, Roshan Sevalia
The Wi-Fi Attack Recognizer and Notifier (WARN) aims to establish a wireless network monitoring system for detection of attacks on Wi-Fi IoT devices. Millions of homes use smart home devices, and many of these are for security. However, these devices are vulnerable to attacks that can disable them or compromise their data confidentiality. WARN is capable of detecting two of these attacks: deauthentication and key reinstallation (KRACK). Deauthentication attacks hoax devices into disconnecting themselves from a network, and KRACK manipulates the authentication protocol of Wi-Fi devices to see unencrypted data. WARN uses Raspberry Pis equipped with long range Wi-Fi antennas to detect these attacks, and users can interact with the system via an iPhone app. In building this project, we discovered that many of the top selling smart home devices are vulnerable to Wi-Fi attacks, so we provided a way for people to know when their devices are under attack. While WARN is not a product ready for commercial manufacturing, this project aims to bring awareness to these attacks, and prove that a low cost solution is possible. The code and detailed installation and usage instructions for WARN can be found publicly at https://github.com/SIOTLAB/WARN.
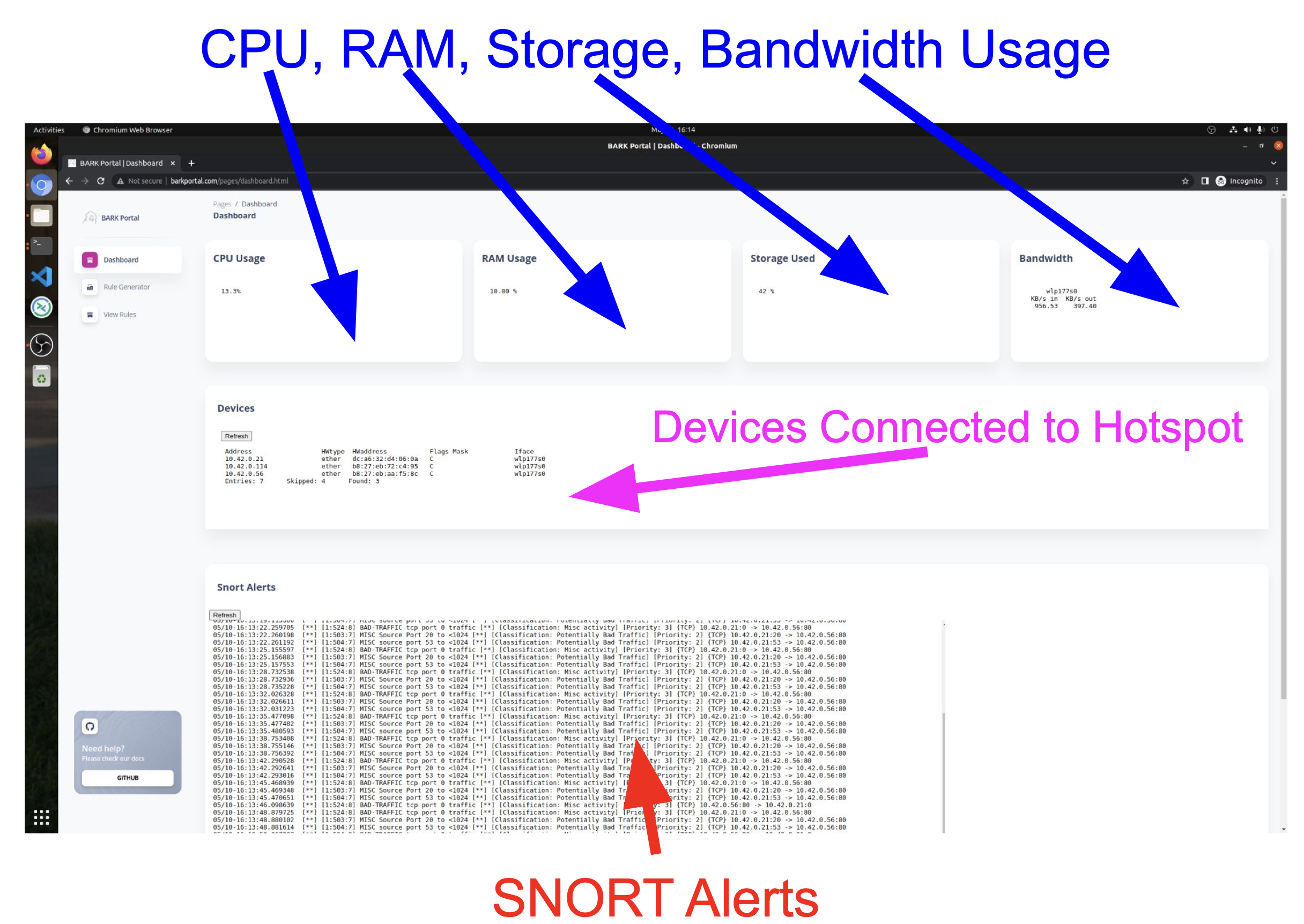
BARK: A Programmable and Extendable Smart Home Network Security System
Rahul Mannikar, Sukanya Tiwari
Nowadays, home networks heavily comprise of smart devices, which provide con- venience to users. Due to the lack of unified smart home security, devices are vulnerable. Our solution, BARK, is a home network security system tailored to smart home devices. This multifaceted system comprises of a SNORT-based packet snifferer and a user friendly web portal for monitoring network activity. The SNORT- based software uses rules to filter trac and block any attacks.
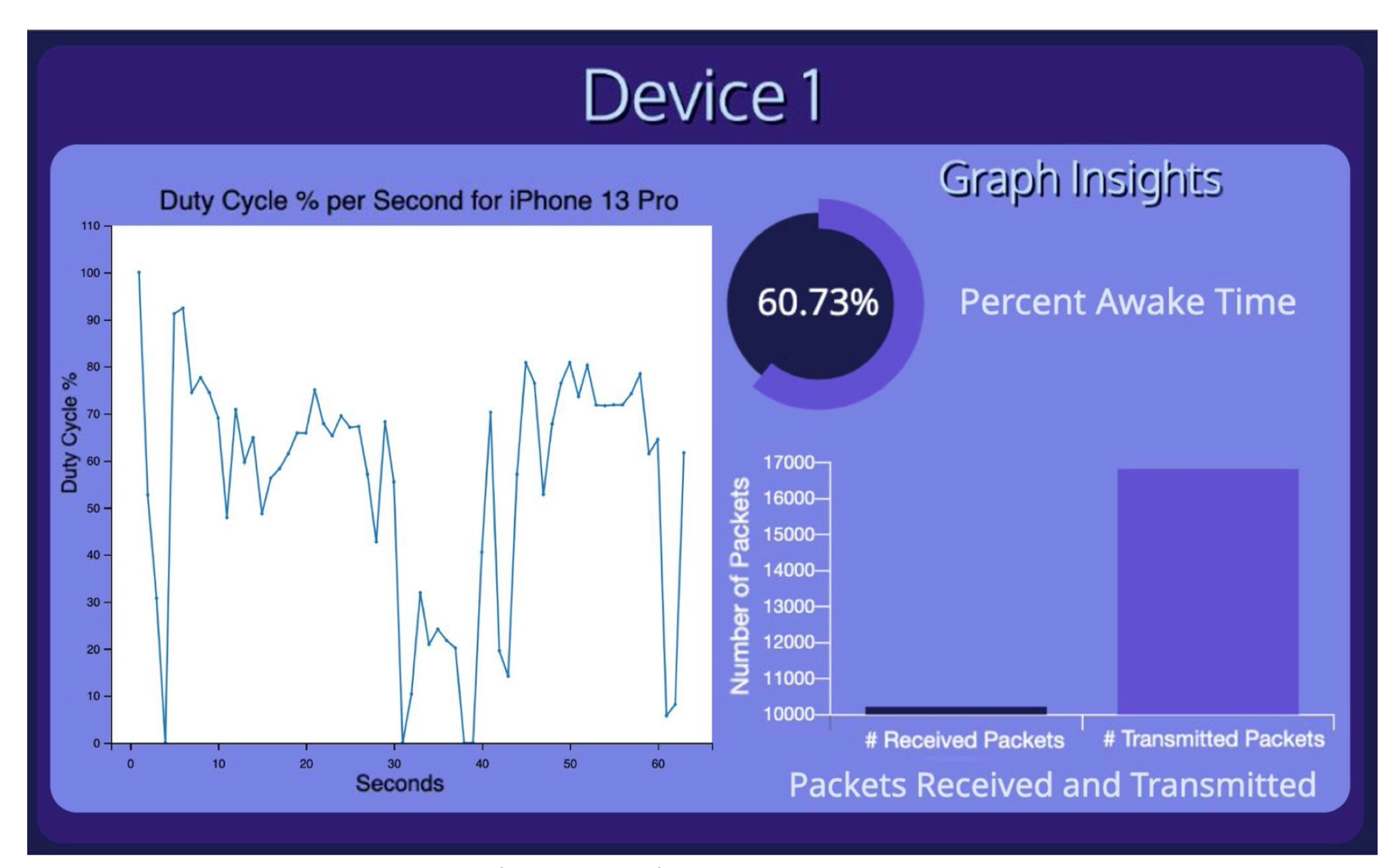
EMT: Software-based Energy Management Tool for WiFi IoT Devices
Aastha Chawla, Nidusha Kannan, Sreya Goyalia
Many WiFi-based IoT (Internet of Things) devices rely on limited energy re- sources such as batteries or energy harvesting. Although monitoring and studying the energy consumption of these devices is essential, the use of external, hardware- based energy measurement tools is costly, non-scalable, and introduces many chal- lenges regarding the connectivity of such tools with devices. In this thesis, we propose EMT, a novel tool to collect, analyze, and monitor the power cycles of IoT devices without the need for any external tools. The basic idea is to modify the WiFi Access Point’s software to keep track of the power status of devices reported in packets. EMT also includes back-end and front-end components for data storage, analysis, and visualization. We demonstrate the effectiveness and features of EMT via empirical evaluations.
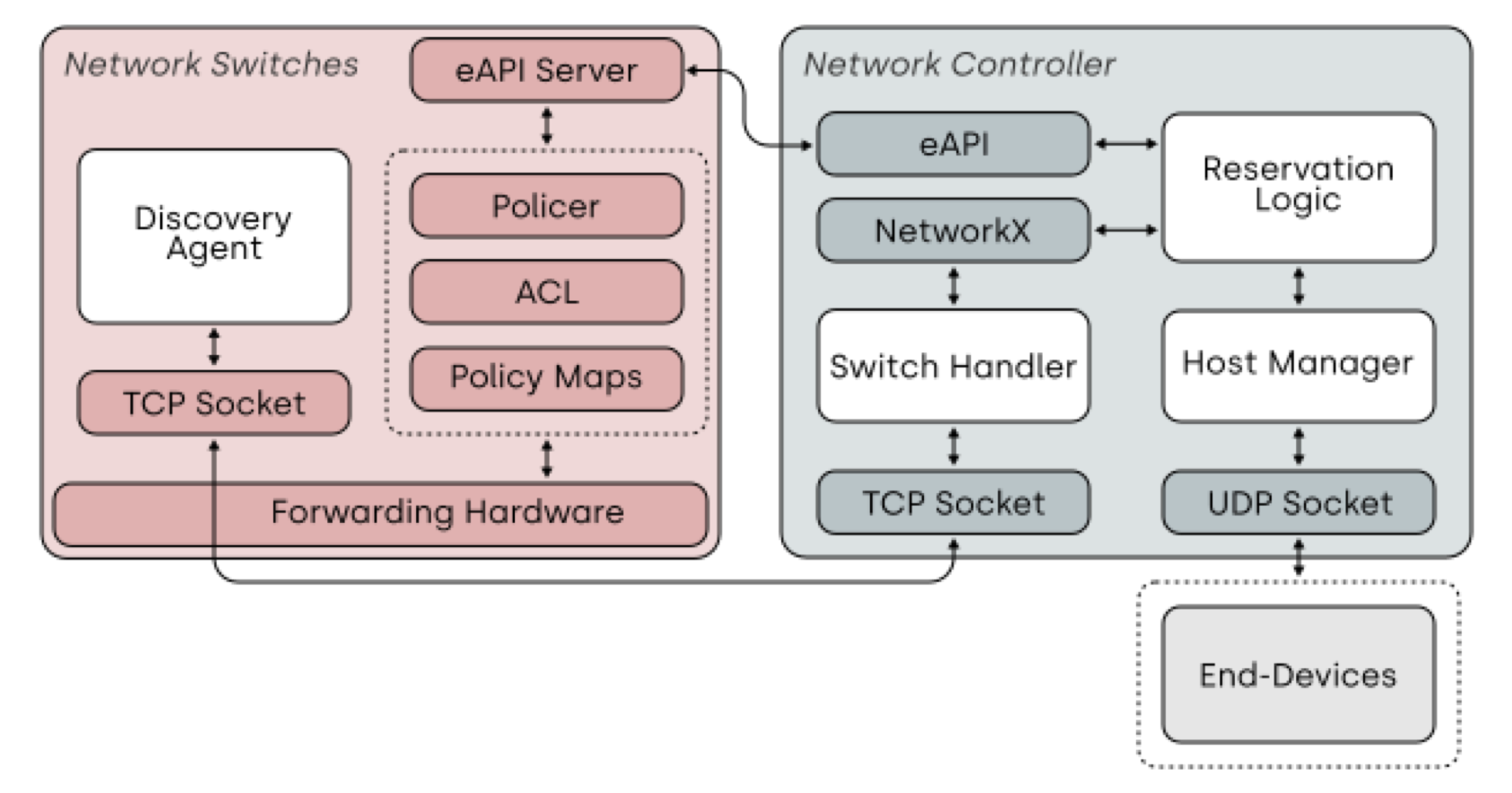
BRASS: Bandwidth Reservation on Arista Switching Systems
Angelus McNally, Conrad Park, Tyler Tivadar
As networking technologies in the fields of Cloud, Fog, and Edge computing continue to gain popularity and widespread adoption, their contributions to network traffic load and congestion in their respective data processing layers are expected to increase. The implication of this inevitable change is that overall traffic congestion is expected to increase, especially in Local Area Networks (LANs). As a consequence of this congestion, network performance is expected to decrease, and the best effort nature of network traffic means that there is no guarantee that applications will be able to communicate at the rates they require for operation. This could prevent certain networking applications from meeting their operational requirements. To address this issue, we propose a resource reservation controller to remotely enforce qualities of service in congested networks and provide bandwidth guarantees on a per-application basis, improving performance of important network communication. The controller provides an effective abstraction for bandwidth reservation that facilitates the reservation process for end devices. It automates the tedious process of establishing policy-based Quality of Service (QoS) in order to slice band- width between different applications. During testing, this network controller was shown to effectively find routes through a network with minimum bandwidth requirements met, remotely send all necessary configuration commands, and create reservations for specific TCP and UDP flows. These reservations were shown to be able to increase bandwidth available for specified network applications at a measurable level.

Detecting the Progression of Osteoarthritis Using Vibration Sensors
Belen Blanco, Joseph Ford, Kailyn Wallace
Over 250 million people are affected by knee osteoarthritis worldwide, causing chronic joint pain and stiffness as well as a general deterioration in quality of life. With existing technologies, it is difficult to predict the evolution of one’s condition and there is often an imbalance between the patient’s pain and the radiographic images, making osteoarthritis difficult to understand and evaluate. We are proposing a wearable, knee sleeve device that uses accelerometer sensors to detect joint stress and friction through frequency readings to more accurately assess the progression of osteoarthritis. Using signal processing and machine learning classification algorithms, our device provides a numerical value correlating with the severity of the patient’s condition.
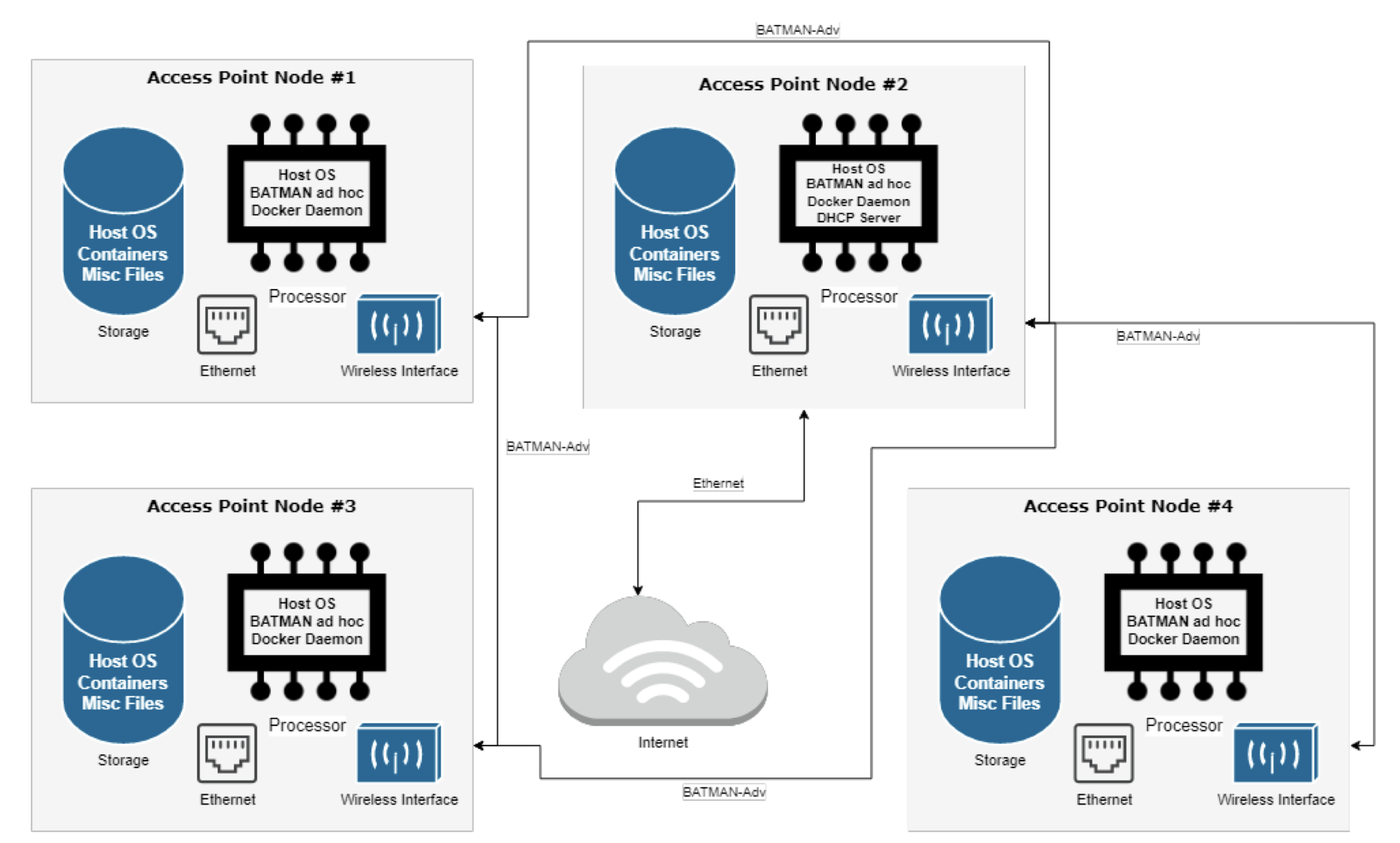
Container Migration in Ad-hoc Wireless Mesh Networks
Gagan Gupta, Kyle Fenole, Siddharth Venkatesh
This project aims to implement container migration on an ad hoc mesh network, which would allow for a mobile fog computing mesh network in areas with no connectivity. This kind of system would allow for a rapidly deployable and mobile compute cluster that could be used in rural scenarios or situations where existing connectivity infrastructures are out of commission i.e. disaster recovery. We use technologies like Docker, CRIU, and batman-adv to create a mesh compute network that is decentralized, flexible, and consistent. Docker with CRIU facilitates container live migration by checkpointing a container in one network node and restoring that container in another node. The batman-adv protocol routes network traffic on layer 2 therefore allowing any layer 3 protocol to be built on top of the existing network. Since this system is aimed to be used in rural areas/areas with no connectivity, power and time considerations were measured and analyzed to ensure reasonable mobile applications were possible.
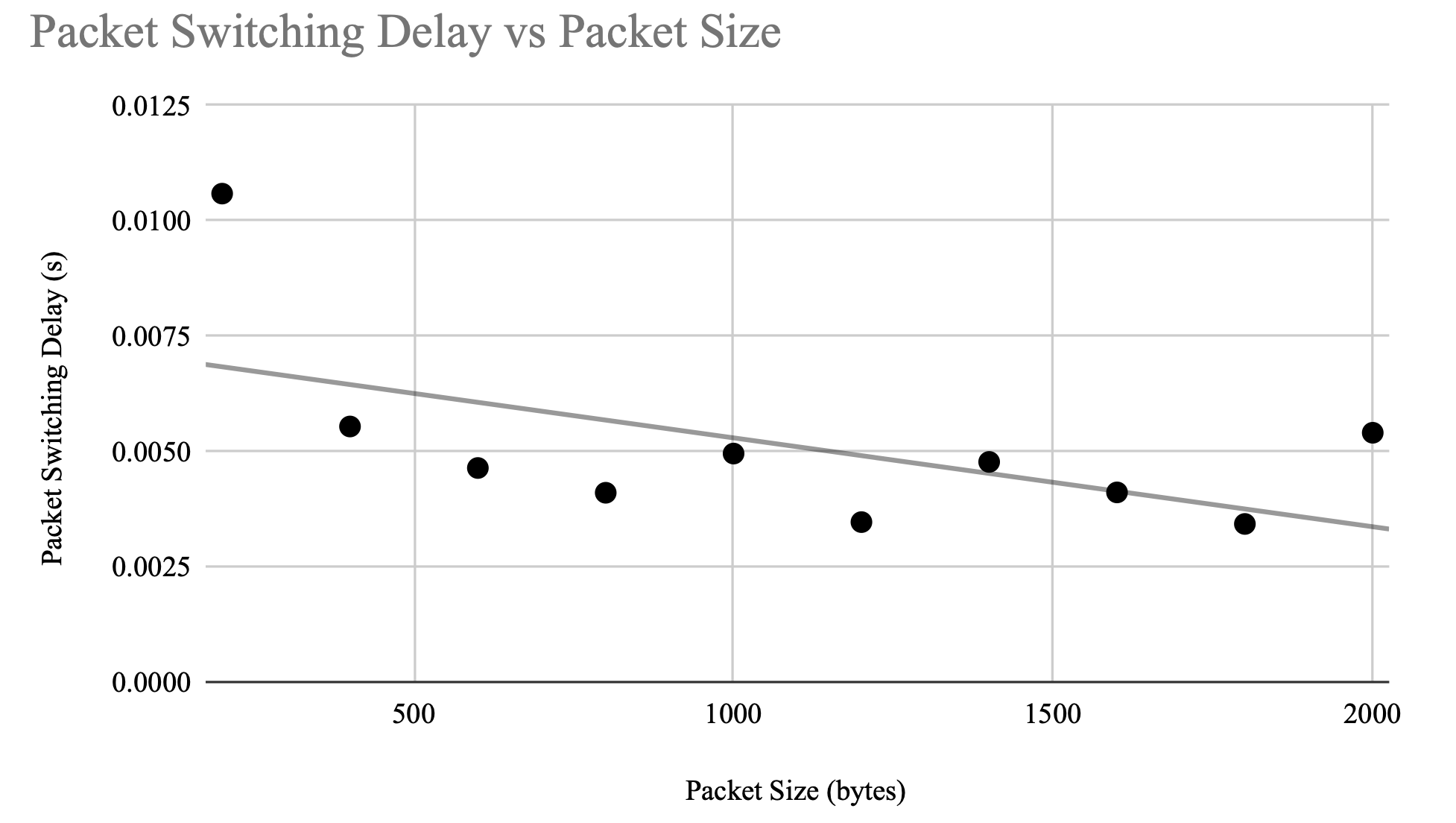
NetCon: Dynamic Resource Allocation to Containers Running on Network Switching Appliances
Siena Hanna, Justin Lee, Tania Pham
A WiFi Access Point (AP) is an important technology that switches data packets to transmit and receive wireless signals to create WiFi. These Access Points (AP) can have powerful processors, but they are idle most of the time. Instead, these idle processing resources could be redirected to run containers for low-latency applications. However, it is essential to ensure that the AP does not suffer performance issues as a result of running containers. The main function of APs is to switch packets, and this function must be preserved while containers are running. In this thesis, we propose a method, NetCon, to measure packet switching delay and allow containers to run on APs only when there are available resources and low traffic. This would allow APs to be leveraged as edge devices for low-latency applications while also maintaining their primary function as packet switching devices by ensuring that packet switching delay is not adversely impacted by running containers.
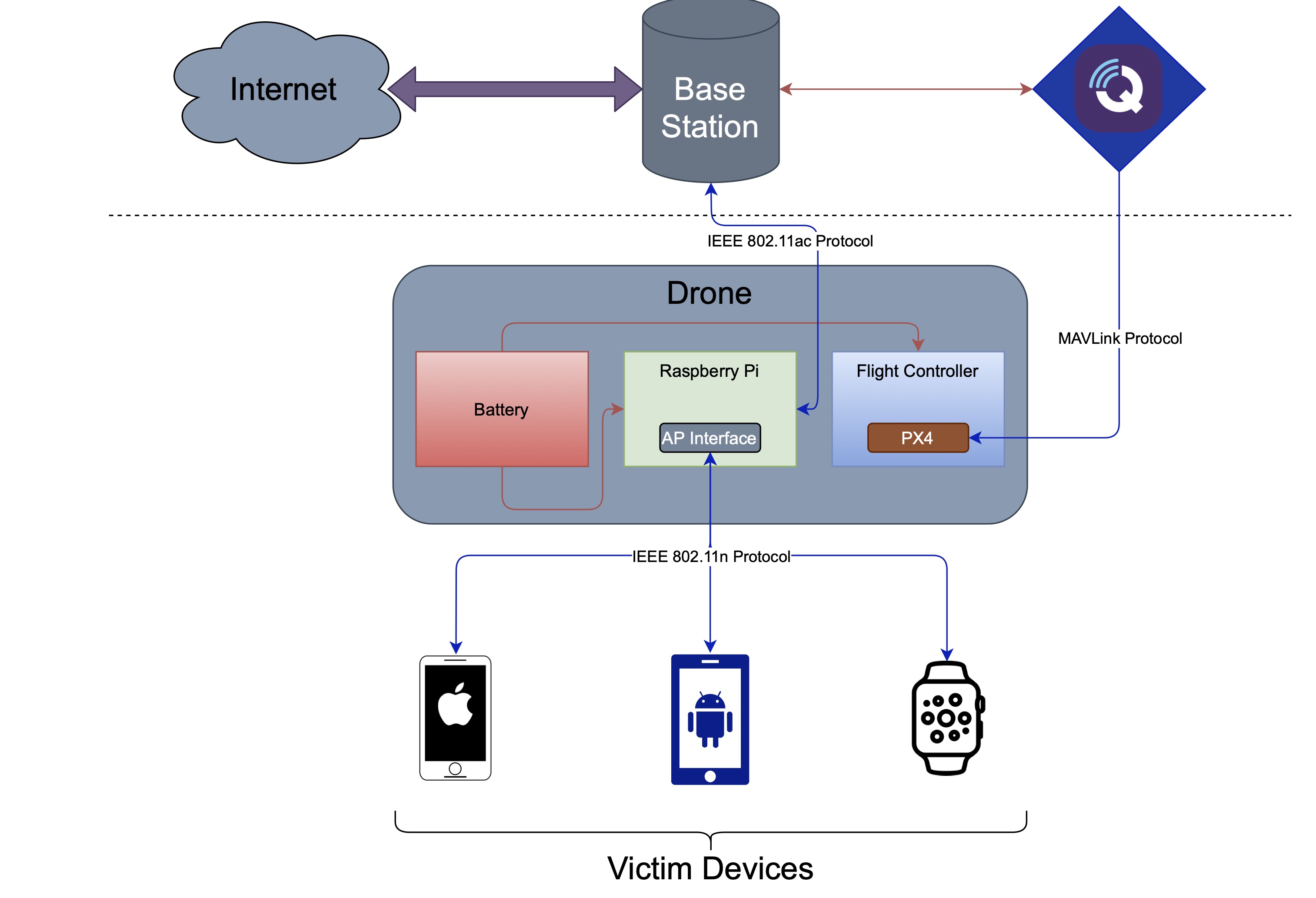
Drone-based Wireless Communications for Disaster Recovery
Cameron Burdsall, Mark Rizko
This project aims to develop a drone system that deploys a wireless mesh network over a disaster recovery area. The system aids in the process of finding survivors by using wireless communications to identify where victims are and allow authorities to send out alerts to people in the area. We also add a device detection feature that allows the drones to passively look for users' devices through WiFi and Bluetooth Low Energy; giving disaster responders the ability to identify specific devices, locate zones where victims lie, and discern a rough population estimate of that area. Those who find themselves in the middle of a disaster situation can use their own devices to establish a connection with the outside world. Under a mesh topology, the drones act as network nodes that enable a more resilient configuration. The drones will be flying above an area to provide wireless connectivity for first responders and those in distress, ensuring reliable detection and a critical communications pipeline when needed the most.
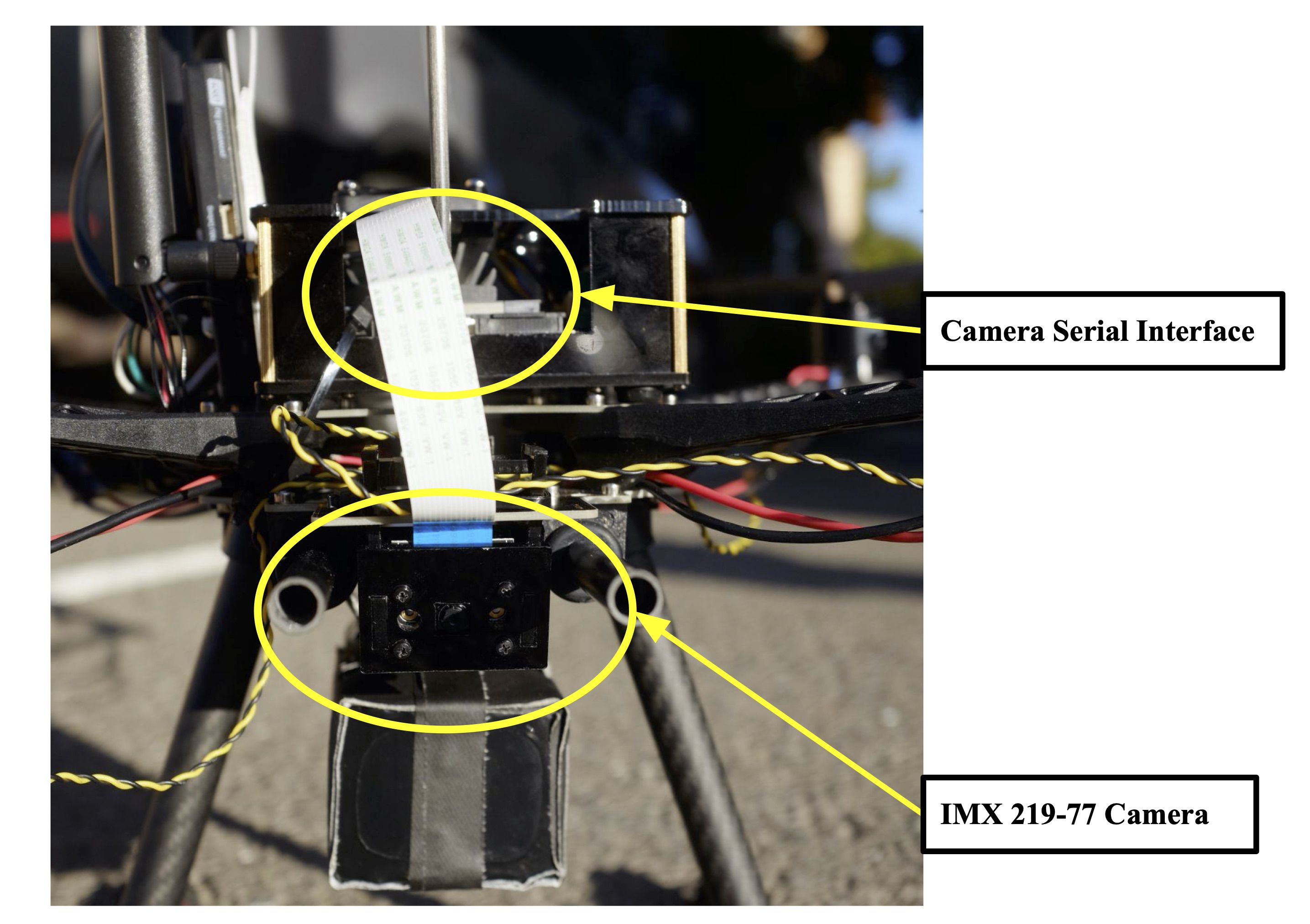
Enhanced Sensing Methods for UAV-Based Disaster Recovery
Connor Azzarello, Ruchir Mehta, Chris Gerbino
Natural and human-caused disasters devastate and displace civilian populations. Over the past century, the rate at which these catastrophes occur has increased dramatically. Climate change and unsustainable human behaviors are significant contributors to natural disasters; therefore, this upward trend will likely continue.
Unmanned aerial vehicles (UAVs) are commonly used to assist first responders during disaster response. The existing UAV technologies focused on disaster recovery have proven to be quite effective; however, they are cost-prohibitive, limiting their use in developing world regions. Unlike the existing UAV-based disaster response technology, we propose a solution that enables indigenous first responders to reap the benefits of UAV-based disaster response technology.
We have created a UAV system with comparable flight time and flight capabilities as the existing industry-standard solutions through an extensive evaluation of cutting-edge single-board computers, UAV hardware, and computer vision models. Additionally, our system capitalizes on the functional drawbacks of the current solutions. It is more modular, allowing for a single UAV to be used in various disasters, and it boasts the capability of real-time computer vision. Most importantly, our system can be recreated for one-eighth the cost of a consumer alternative with similar functionality. As a result, first responders in low-resourced regions have access to affordable disaster response technology that can be used to save lives.
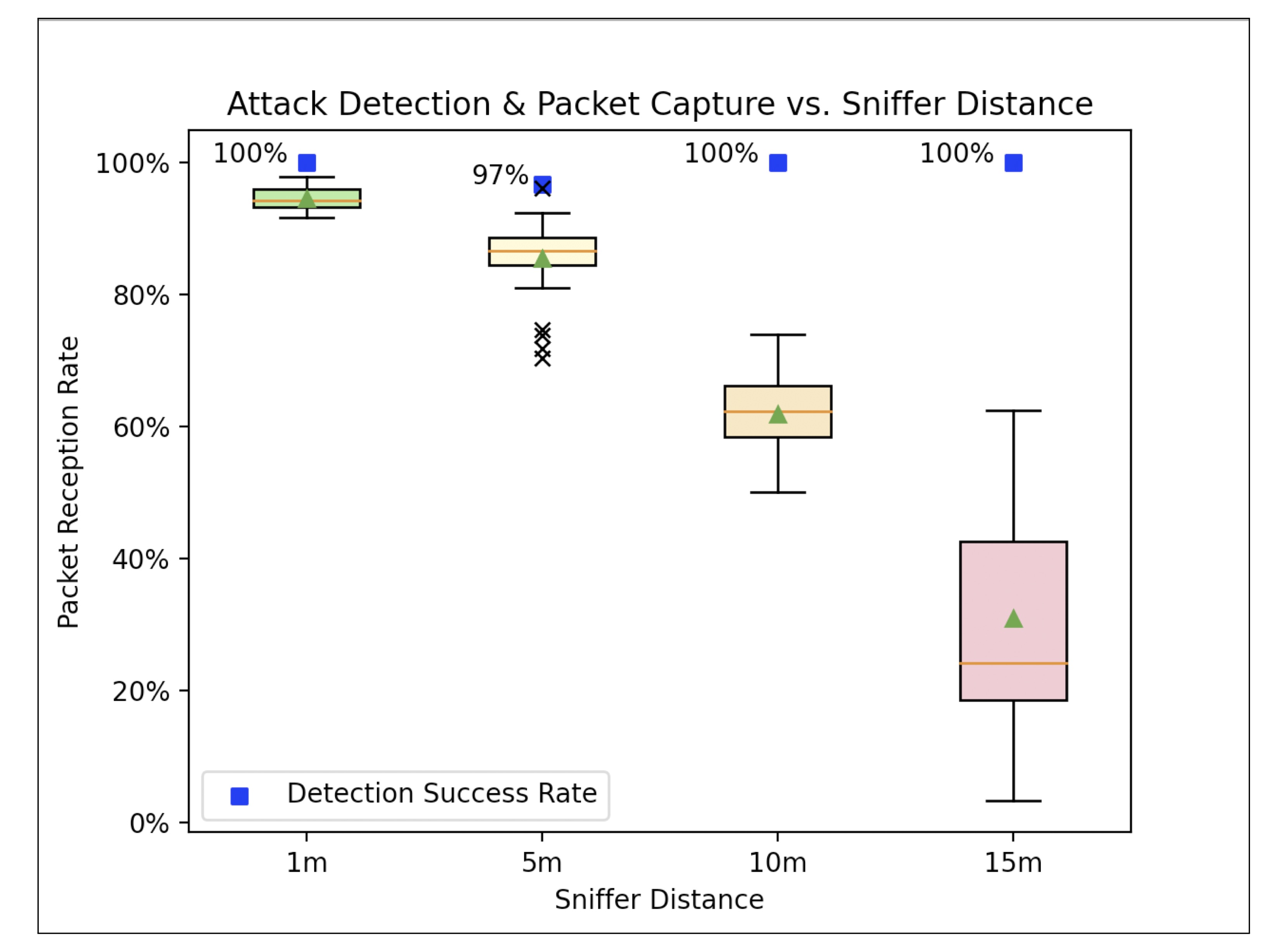
Jamming Attack Workaround Study
Soren Madsen, Jack Schoen
The Internet of Things (IoT) is a fast-growing industry with solid footholds in the smart home market featuring devices such as the Amazon Echo, Ring security cameras, smart TVs, and much more. However, it doesn't stop there; the industrial sector has begun using smart devices for measurement, automated tasks, and time-sensitive communication. Many of these devices have become reliant on WiFi technology and are vulnerable to attacks on the protocols' security.
In this project, we discuss the details of the de-authentication attack on WPA and WPA2 systems and propose a solution for detection and recovery in IoT networks, all included in a single, easy-install device. We evaluated our solution in a smart home environment against variations in packet reception rate and concluded that our system is effective for small smart home networks. In addition, this solution can be modified in various ways to further the field of IoT security and provide manufacturable, easily accessible smart system security solutions.
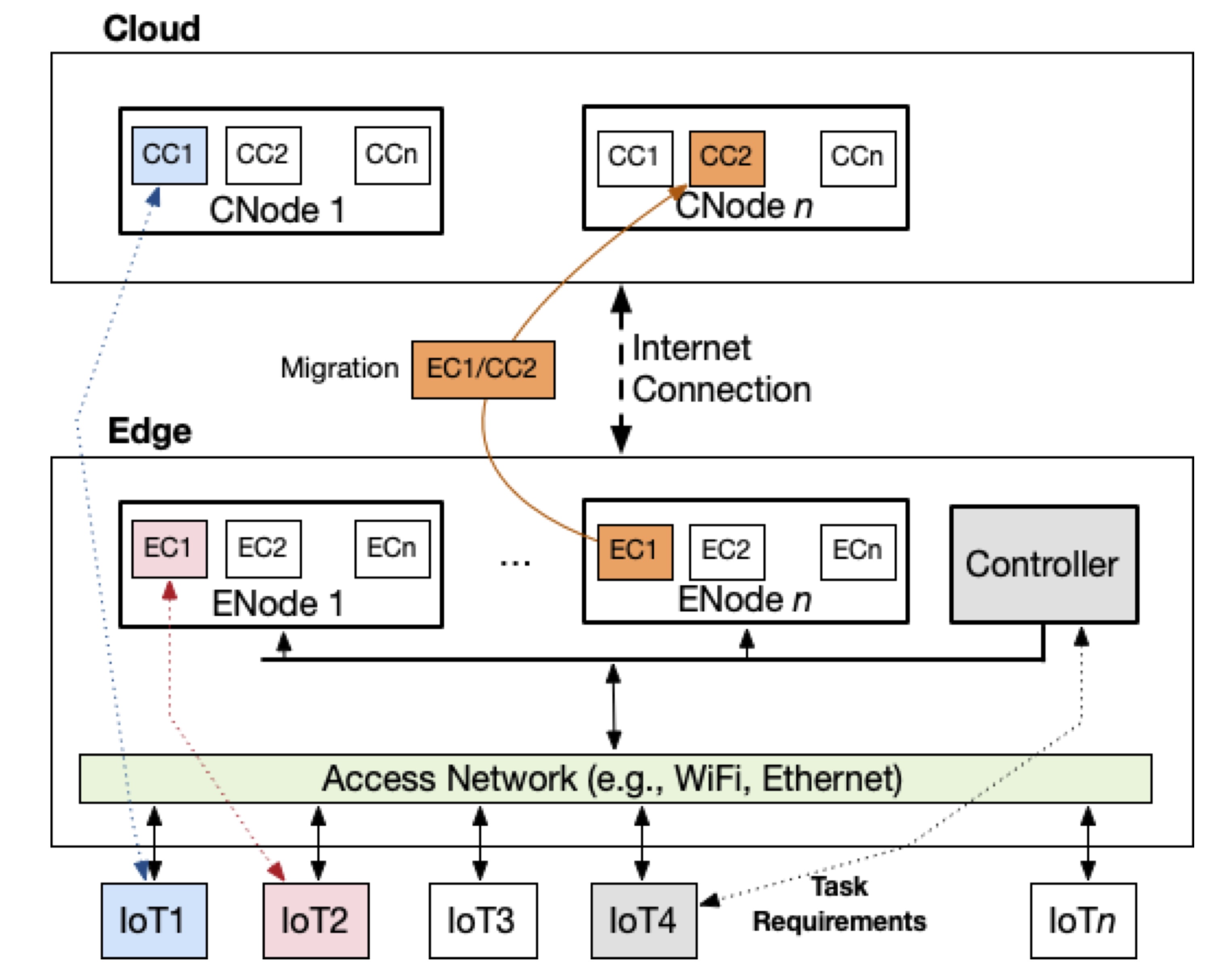
Seamless Container Migration Between Cloud and Edge
Angeline Chen, Jonathan Yezalaleul, Aditya Mohan, Tamir Enkhjargal
Considering the limited resources of edge devices, it is essential to monitor their current resource utilization and device resource allocation strategies that assign containers to edge and cloud nodes based on their priority. Edge containers may need to be migrated to a cloud platform to reduce the load of edge devices and allow for running missions critical applications. In this case, we propose a prioritization method to exchange containers between the edge and cloud while assigning delay-sensitive containers to edge nodes. We evaluate the performance of running Docker container management systems on resource-constrained machines such as the Raspberry Pi. We propose methods to reduce the overhead of management and migration depending on the workload type.
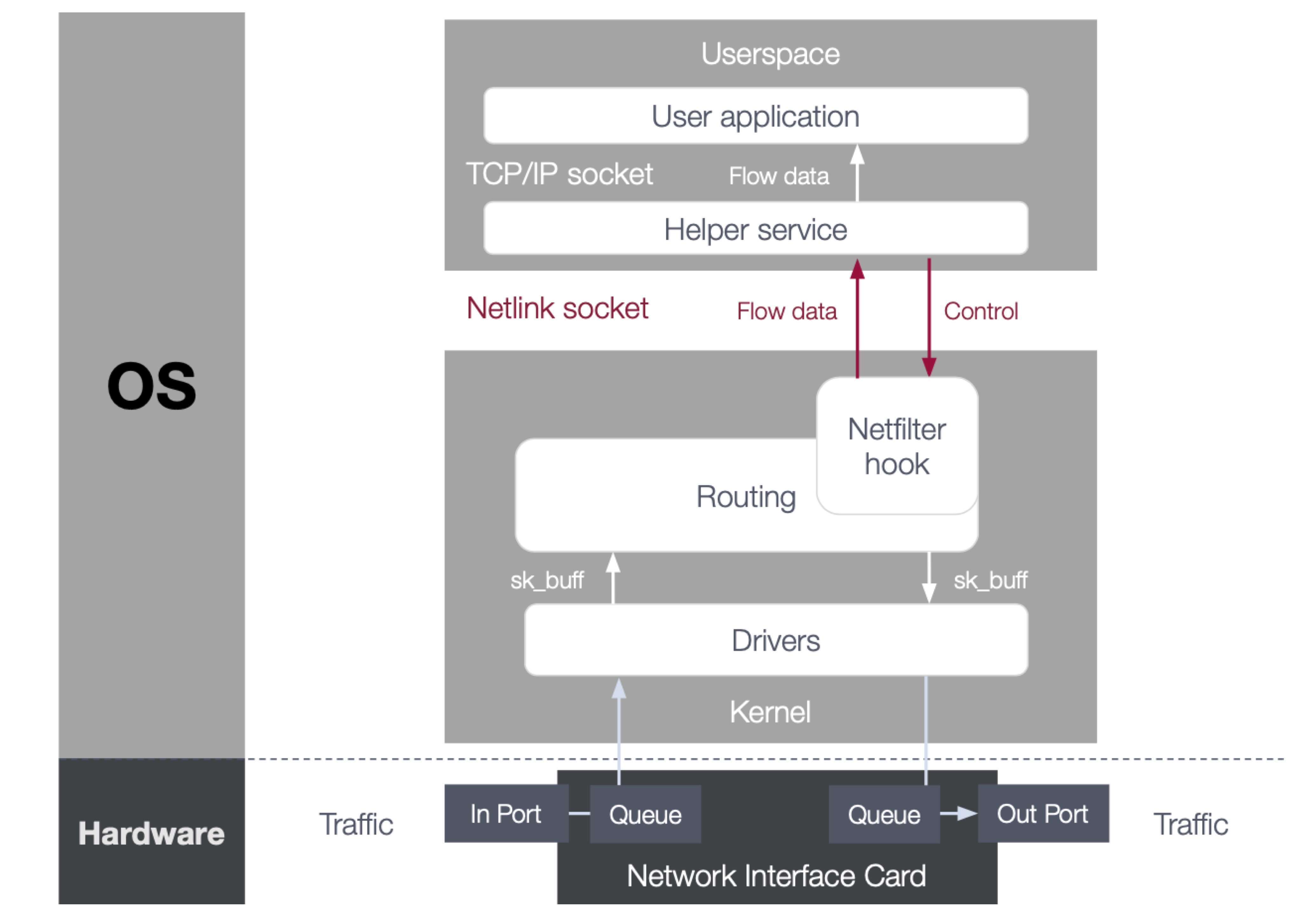
HUSK: High-level Network Feature Utility for Security-based Kernel
Shaunak Mashalkar, Dillon Leigh
In network security operations, real-time analysis is highly intensive and often requires dedicated hardware. Typically, raw network data must be transferred from low-level switching mechanisms to extract more helpful information. Thus, the truly responsive security analysis is gate-kept to commercial and research settings capable of affording the proper infrastructure. We propose HUSK, a system that moves processing technology to the kernel level, thereby considerably speeding up real-time network analysis and lowering the barrier of entry for network analysis.
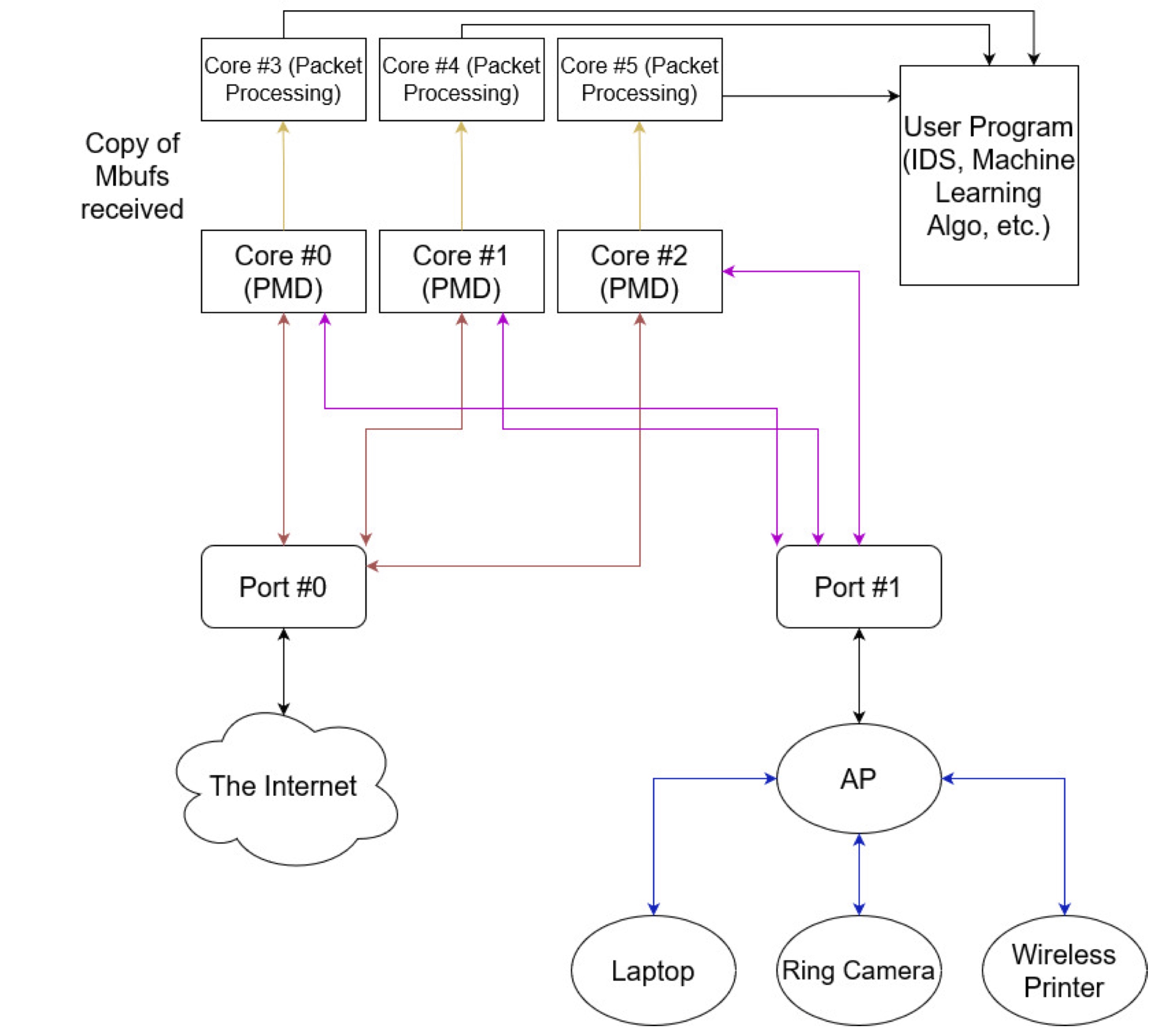
Deep Packet Inspection on Edge Devices using DPDK
Jordan Mortif, Kade Harmon
The number of Internet of Things (IoT) devices connected to enterprise and home networks has increased drastically. Given the prevalence of IoT devices worldwide, the tools used to measure such devices do not scale with the current rate of IoT growth. The Data Plane Development Kit (DPDK), initially developed by Intel, offloads packet processing from the operating system. We utilize DPDK and propose a feature collection system to collect and analyze packet data in real-time and reduced overhead. Additionally, developers can attach their analysis engines directly onto the feature collection engine through a simple programming interface.
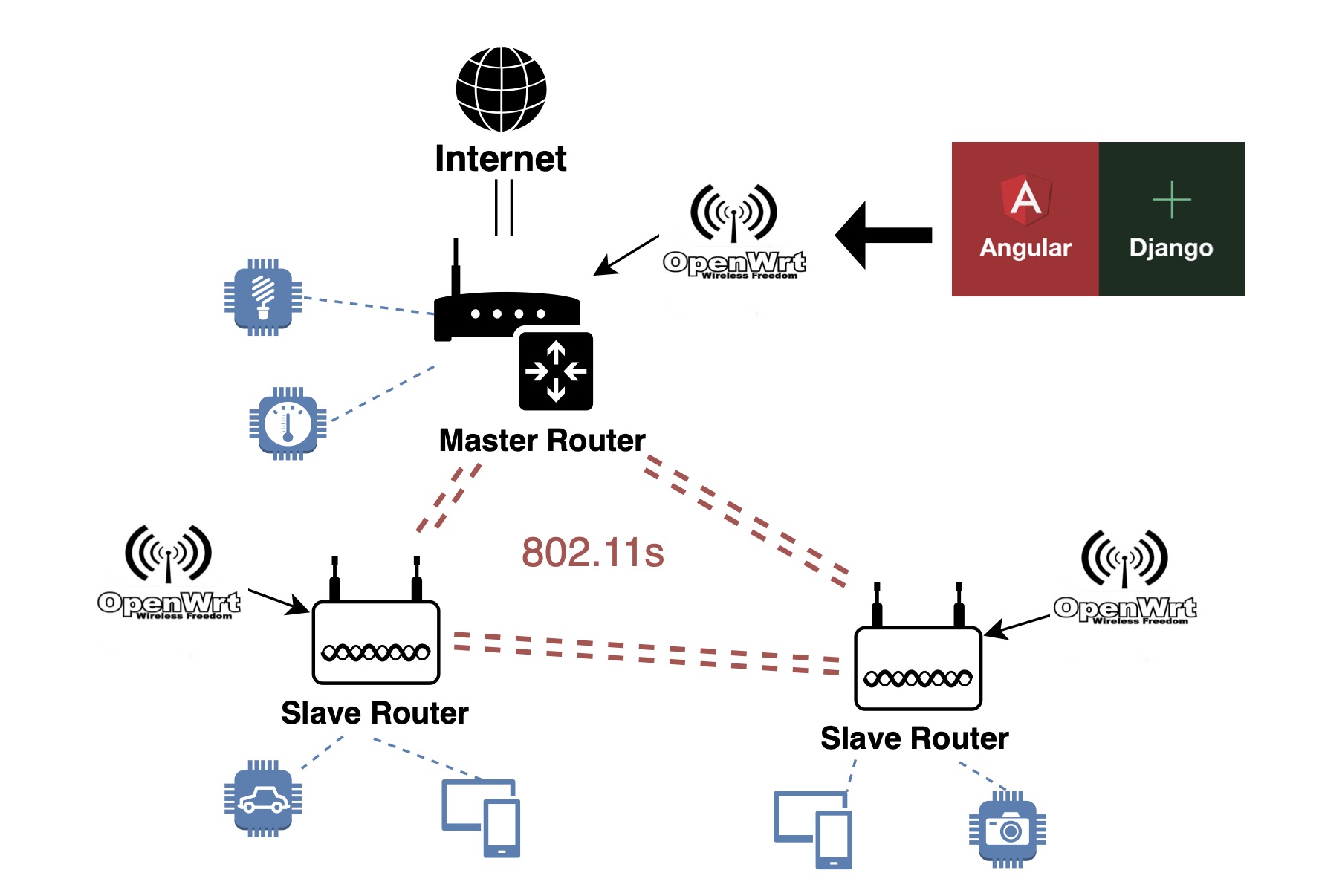
CentriFi: A Centralized Wireless Access Point Management Platform
Andreas Anderhub, Zac Wilson
With the ubiquity of wireless end-devices, more strain is placed on standard network deployment architectures. Mesh networks have started to rise in popularity to meet the needs of modern wireless networks. However, the existing solutions for deploying and centrally configuring mesh networks leave much to be desired, as most are too expensive or cumbersome. This work showcases a solution to this problem, CentriFi—an open-source platform built to run on OpenWrt access points, providing a quick and easy way to set up and configure mesh networks in a central location using the 802.11s standard. CentriFi provides a web-based front-end for configuring the most crucial settings. Further, the system allows for greater expandability by providing a platform in which other configuration feature can be added by the open-source community in the future.
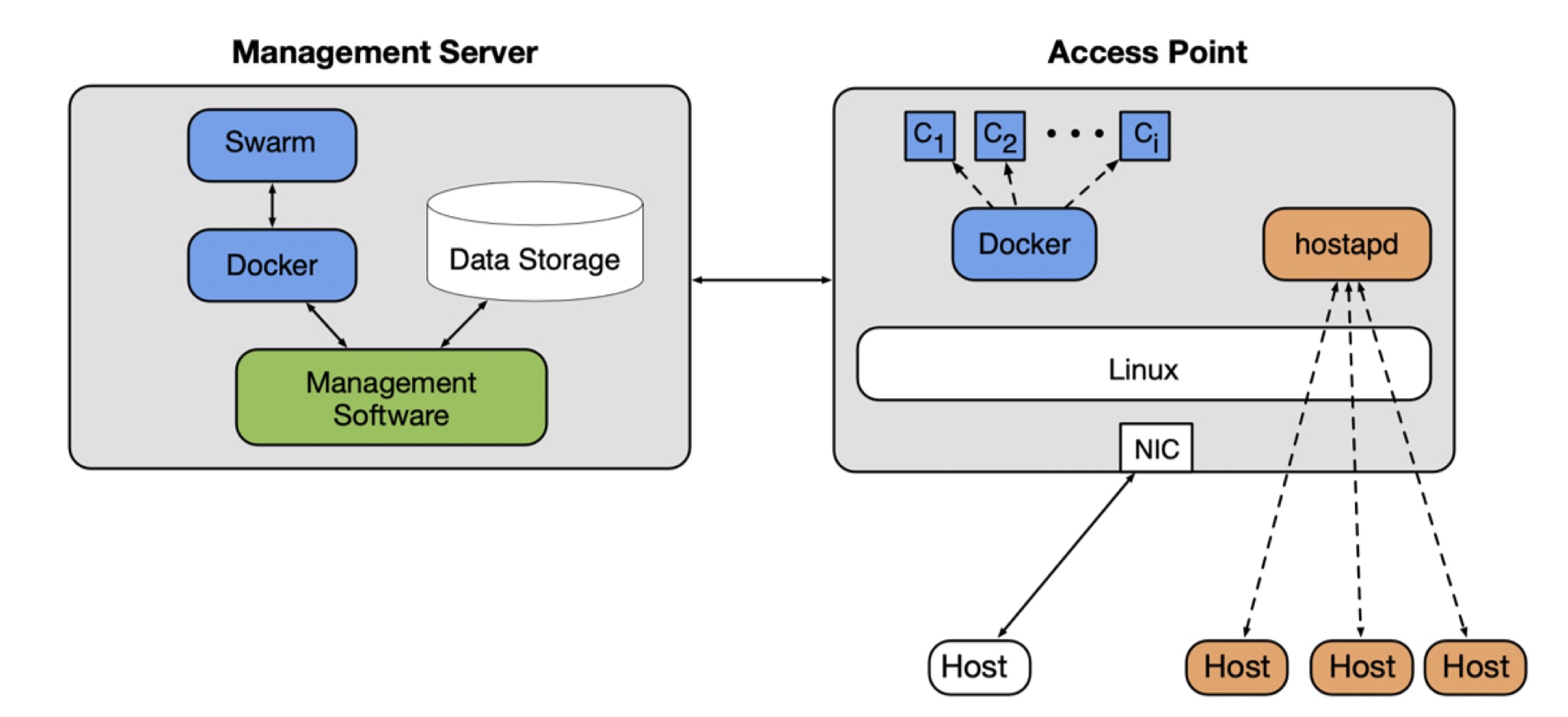
EdgeAP: Enabling Edge Computing on Wireless Access Points
Christopher Desiniotis, Justin Majors, Cyrus Miremadi
With the rise of the Internet of Things (IoT) leading to an explosion in the number of internet-connected devices, the current cloud computing paradigm is approaching its limits. Moving data back and forth between its origin and a far-away data center leads to privacy, latency, and energy consumption issues. Edge computing, which instead processes data as close to its origin as possible, offers a promising solution to the pitfalls of cloud computing. Our proof-of-concept edge computing platform, EdgeAP, is a programmable platform for delivering applications on wireless access points. The use cases of the platform will be demonstrated via an example application. Additionally, the viability of edge computing on wireless access points will be thoroughly evaluated.
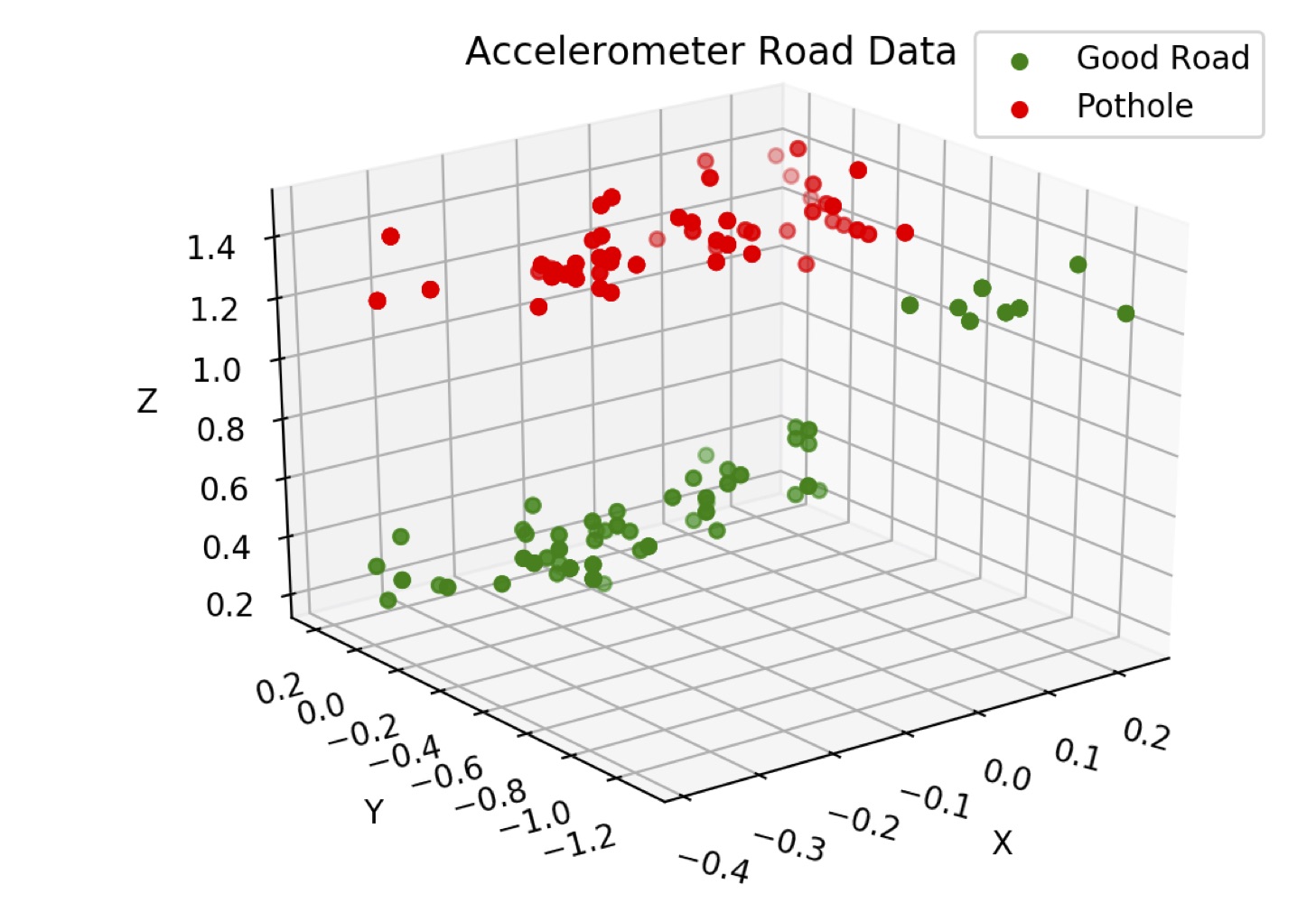
Drive Health: Road Condition Detection
Peter Ferguson, Brian Walker
Roadways play an essential role in today's society by contributing to economic growth and development, providing social benefits and fast routes to travel around efficiently. With more and more cars on roads, the quality of the streets is deteriorating faster than before. This decrease in road health contributes to hazards such as potholes and can cause significant damage to vehicles on the road. Currently, improving and monitoring roads' health is done infrequently and is time-consuming for the government. Therefore, many road quality issues are manually reported by the people who drive on them. This requires filling out forms or making phone calls while also remembering the pothole or road hazard location. In this work, we present Drive Health, a system developed to monitor roadways' health and inform the transit authorities of poor road quality. This device also can advise the driver on how to be a safer and more efficient driver. Drive Health includes a smart sensor and performs machine learning on accelerometer data to process and analyze the device without using the cloud. If the system determines the data indicates the existence of a pothole, its location is recorded and sent to a web server.
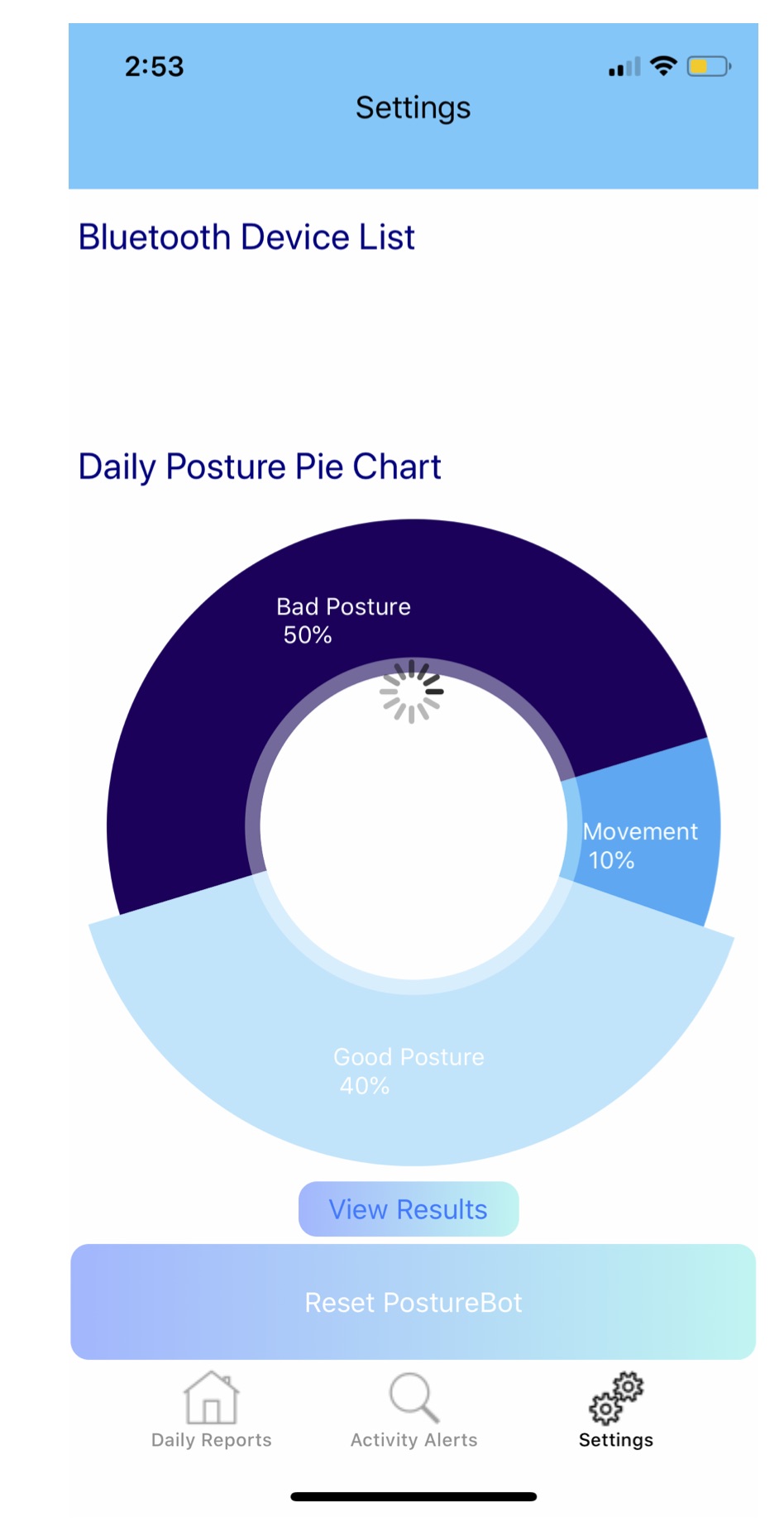
A Low-Cost and Energy-Ecient Wearable Device For Posture Monitoring
George Shappell, Ying Huang, Ali Nazemi
Millions of Americans suffer every year from back problems; now, imagine if there was a way to help track and prevent back problems. Our solution to this problem is PostureBot, a device that will allow its users to correct their back posture and maintain good back posture. In doing so, this device can help elevate and prevent people from developing minor and severe back problems in the future.
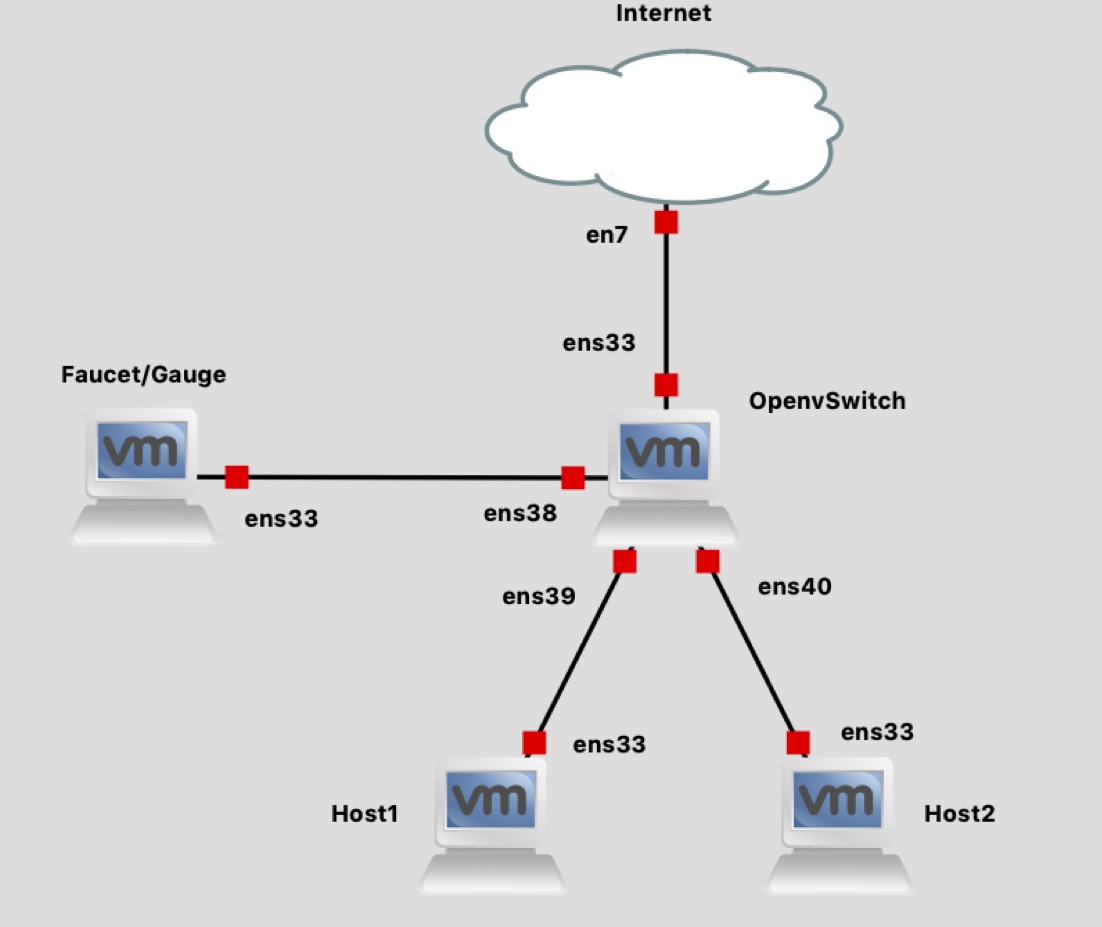
SDHome: Securing Fast Home Networks
Christopher Batula, Holden Gordon, Tianyi Zhao
Distributed denial of service (DDoS) is a highly discussed network attack in Software Defined Networks. Attacks such as the Mirai Botnet threaten to compromise a portion of large networks, including home users. Today, corporations secure their network using enterprise-level software to protect their network from DDoS attacks. But their solutions are meant for large networks and depend on expensive hardware. There are few security solutions for home users, and most are expensive or require a subscription for complete protection. We propose a new solution in the form of a plug-and-play device that will allow home users to control their network easily. We will be using the SDN controller Faucet and the protocol OpenFlow 1.3 to enable software-defined functionalities. In addition to more basic network features such as blocking websites, the device will allow users to receive notifications about possible malicious activities on their network, generate device profiles for all devices on the network, and automatically detect and mitigate flooding attacks using a random forest classifier. We implement our network virtually using Graphic Network Simulator 3.
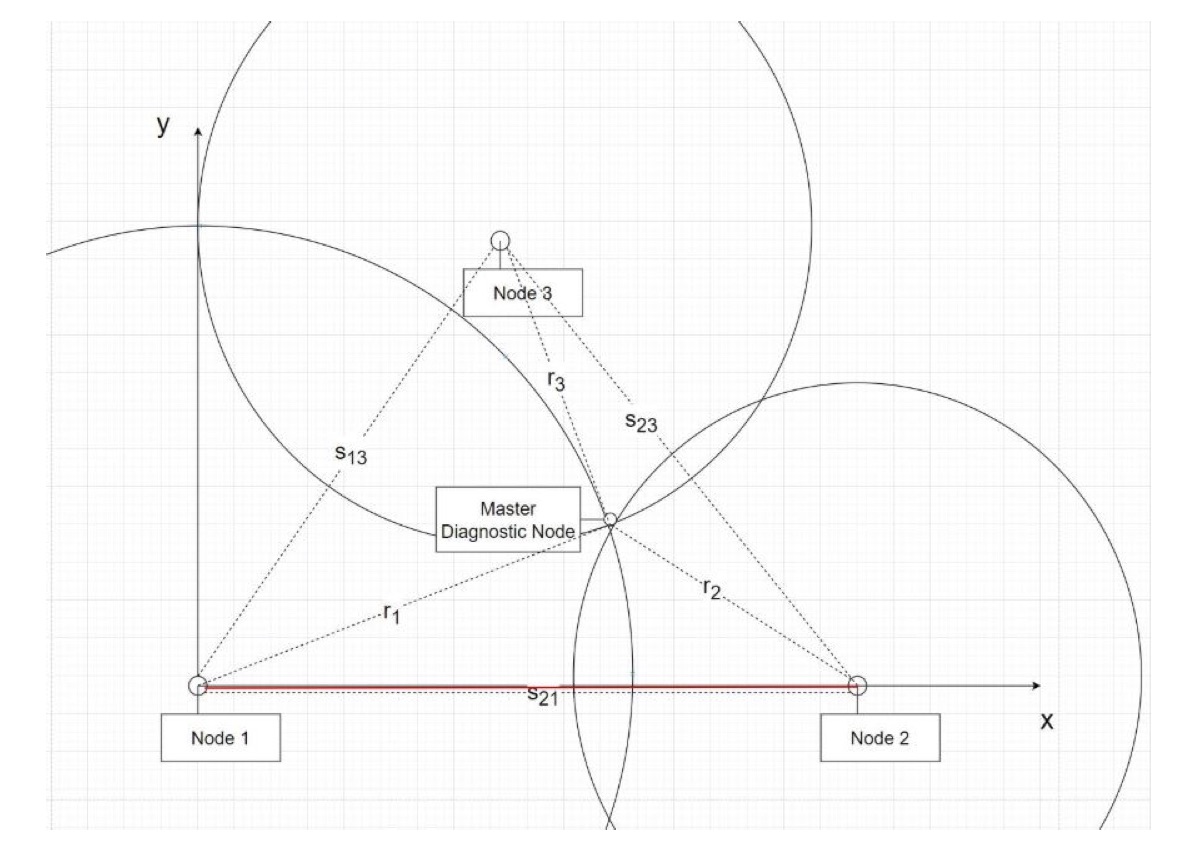
LeaPi: Wireless Diagnostic Assistant
Jeff Collins, Austin Iverson, Collin Seaman, Joseph Sindelar
Nearly every person who uses WiFi on a daily basis has had trouble with a bad connection. Wireless connectivity issues are often difficult to diagnose and fix. Current solutions such as wired extenders and Mesh WiFi commercial packages are expensive, and they do not provide the user with a system that suggests placement of mesh units to maximize coverage. Our solution is an inexpensive and open-source diagnostic tool that maps out WiFi quality and informs the user about interference. With a simple, meaningful display, users will find trouble spots in their house, diagnose why IoT devices are not working, effectively place WiFi extenders and mesh nodes, and more.
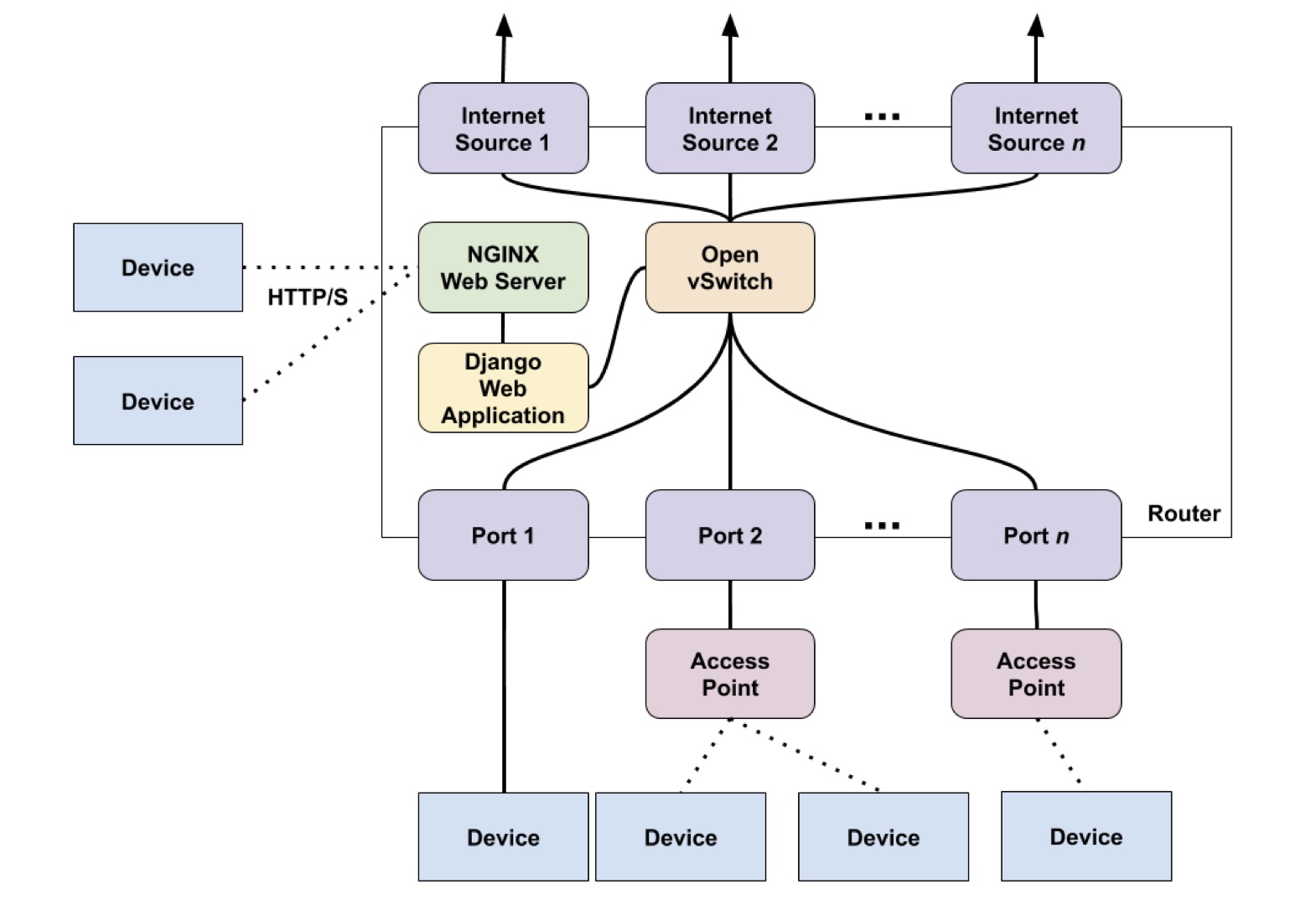
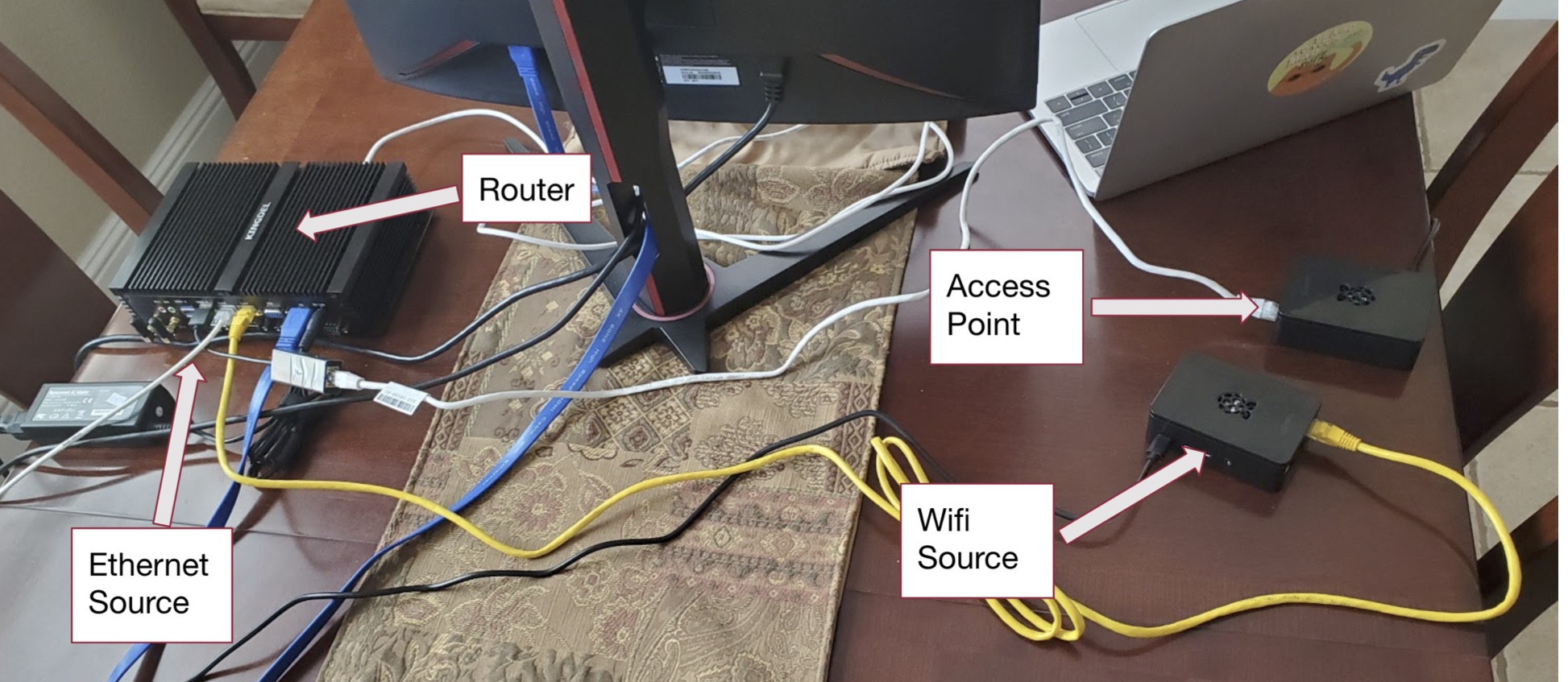
ACAS: Always Connected, Always Secure
Blaise Aranador, Antonio Gigliotti, Shining Liu
There is no place where safety is more important than in the home. Research has shown that home security systems effectively deter burglars; additionally, these security systems allow residents to monitor their property at all times, even while they are away. More and more of these home security devices rely on a stable Internet connection and cannot provide functionality without it. ACAS is a system that helps keep smart devices connected to the Internet, even during a home internet outage. ACAS includes a programmable router that can connect to multiple Internet sources, setting it apart from other routers. ACAS can connect to two or more Internet sources at a time and then broadcast a wireless Internet signal that one's smart security devices (and any other device) can connect to it. The router uses one Internet source at a time to provide a wireless signal for all devices to connect to it. Still, if the Internet source goes down for any reason, ACAS automatically switches to one of the other Internet sources connected to it. This provides a reliable backup and keeps devices connected to the Internet as long as one of the multiple Internet sources connected to the router is up and running. Our system also includes a web application that can configure some aspects of the router and obtain up-to-date statistics about the router's operation. Users can check the network speed of the Internet connection and choose which of the multiple Internet sources is the primary Internet source at any given time.
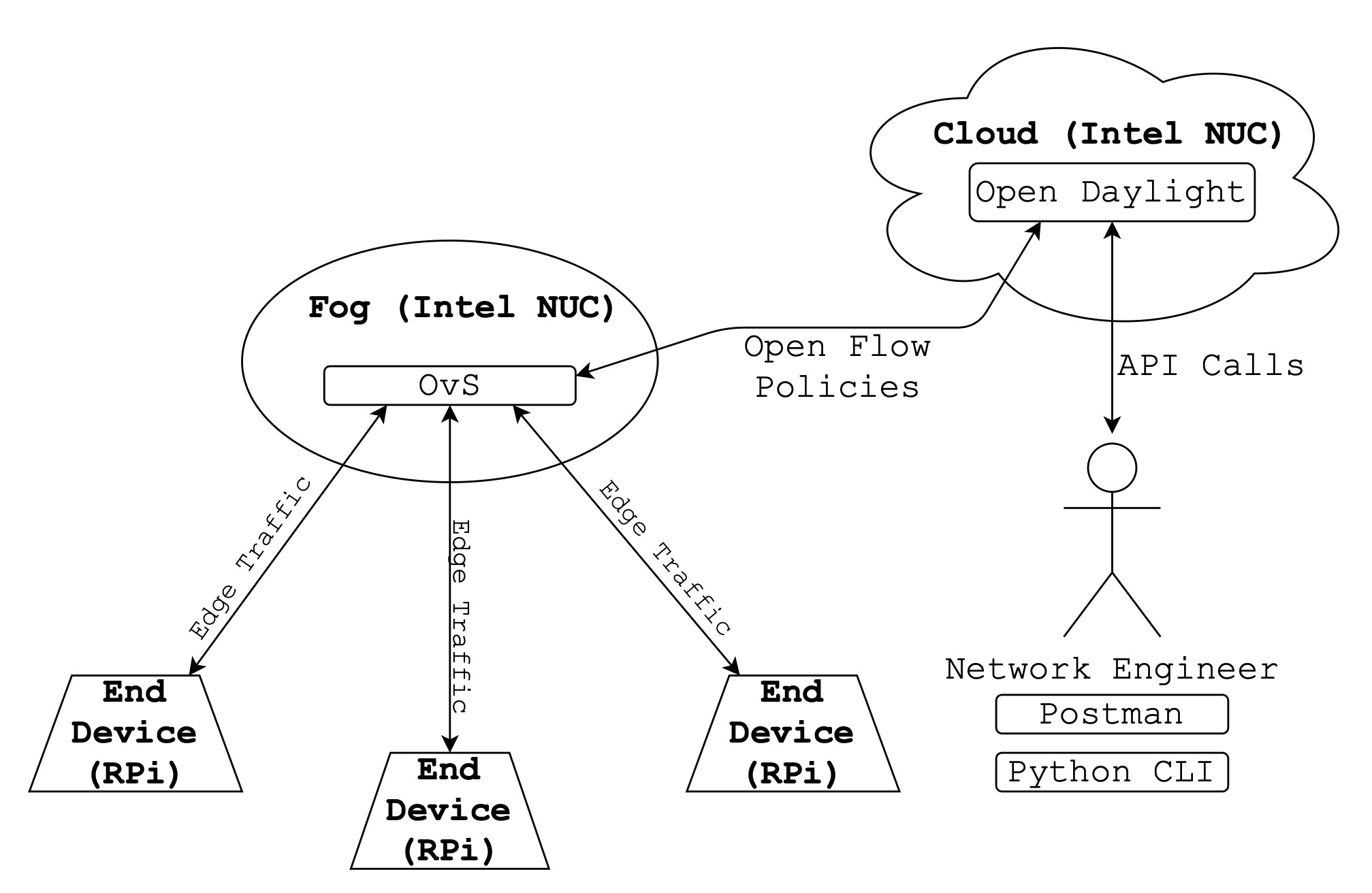
Distributed Firewall for IoT
Ryan Lund, Anthony Fenzl, Chelsea Villanueva
Minimal local resources, lack of consistency in low-level protocols, and market pressures contribute to IoT devices being more vulnerable than traditional computing devices. These devices have various processors and implementations, but they often serve different purposes and generate unique network traffic. Current IoT network security solutions fail to account for and handle both the scale at which IoT devices can be deployed and the heterogeneous nature of the traffic they produce. To accommodate these differences and improve current solutions, we propose implementing a micro-segmented firewall for IoT networks. Unlike traditional micro-segmented architectures, which use a virtual management layer and hypervisors to manage, route, and filter the traffic from VMs, we propose using a cloud-based management layer working in cooperation with fog node filters to manage end devices' traffic. The fog nodes act as the first hop from the IoT devices, filtering traffic according to the rules given to them by the management layer. This decreases packet filtering latency by distributing the computing load and limiting the number of hops packets make for processing. Meanwhile, having a singular management point gives network administrators the convenience of controlling all traffic flows at a moment's notice, as would be the case in a traditional SDN. As a result, this architecture promotes both the adaptability and scalability needed in IoT networks, all while securing traffic flows and minimizing latency.
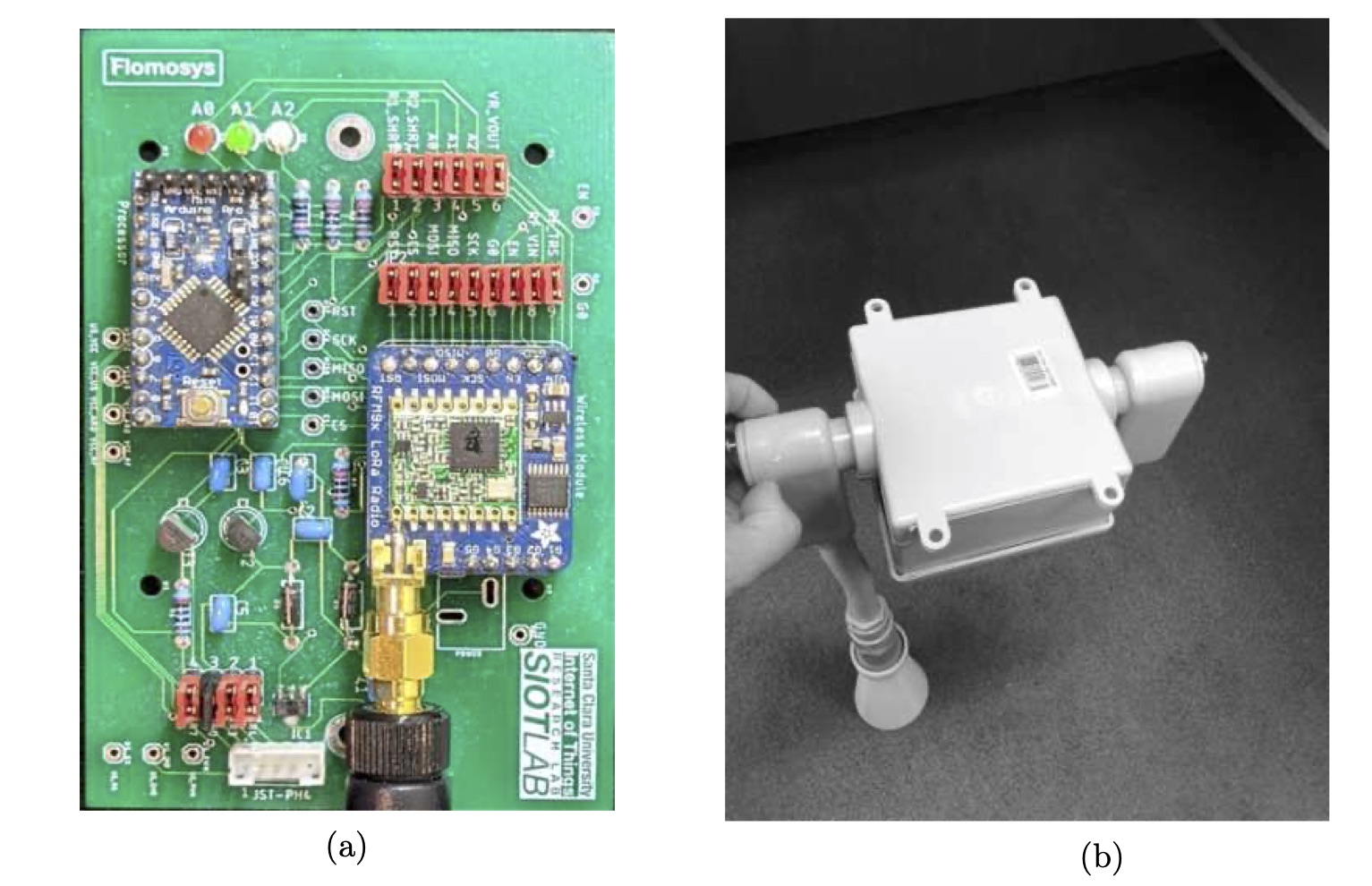
Flomosys: A Flood Monitoring System
Tai Groot
The expansion of the Internet of Things (IoT) has led to numerous innovations in the industry, including improvements to existing systems. Disaster prevention and monitoring systems are prime examples of such systems. Every year, there are significant and preventable financial losses, not to mention the safety hazards caused by floods. To warn people ahead of time, it is possible to deploy low-power wireless sensor nodes to send readings collected across the terrain to a cloud platform, performing pattern analysis, predicting, and alert forwarding to anyone's cellular device. We propose Flomosys, a low-cost, low-power, secure, scalable, reliable, and extensible IoT system for monitoring creek and river water levels. Although there are multiple competing solutions to help mitigate this problem, Flomosys fills a niche not covered by existing solutions. Flomosys can be built inexpensively with off-the-shelf components and scales across vast territories at a low cost per sensor node. This work presents the design and implementation of Flomosys as well as real-world test results.
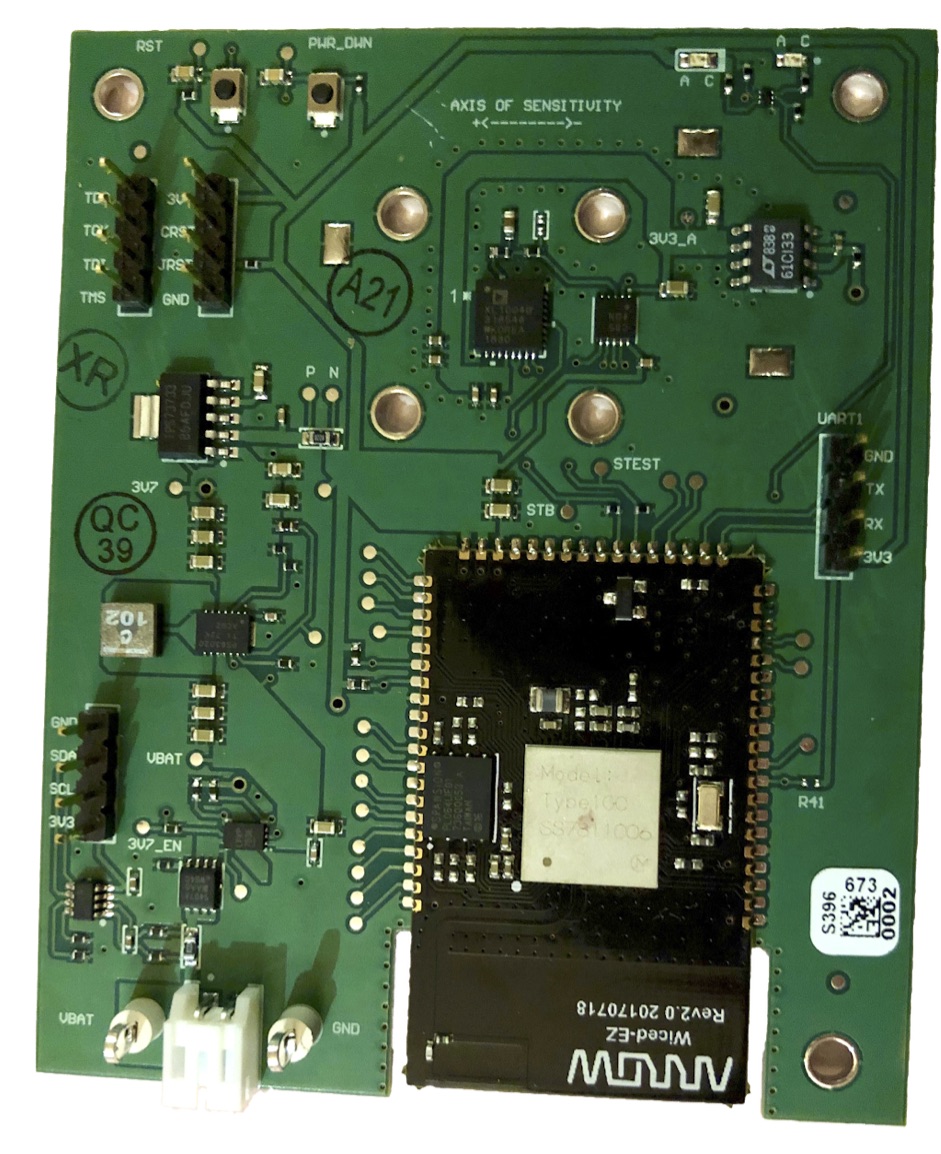
WASP: Wireless Analog Sensor Platform
Cole Hunter, Daniel Webber, Tyler Hack
WASP aims to augment and eventually replace the bulky, costly, and complex data acquisition systems used for vibrational reliability tests on satellites. As a mechanism to guarantee that a spacecraft is mechanically durable and robust enough to withstand the acceleration forces experienced on the vessel during launch, companies conduct vibrational experiments on their spacecraft by subjecting them to high G-force events. Using wired accelerometers connected to obstructive cables, the mounting process and test setups required to perform such experiments are expensive, laborious, and can generate measurement inaccuracies. We developed a low-cost, battery-powered module designed for engineers to replace the current sensors and data acquisition systems with a wireless solution. This will enable precise testing of conditions on a smaller time frame and at a lower cost and help eliminate the disadvantages of a wired system. A custom circuit board has been fabricated containing the critical measurement and processing components required to realize this objective and a complete software solution to facilitate the data transmission to a wireless router over WiFi.
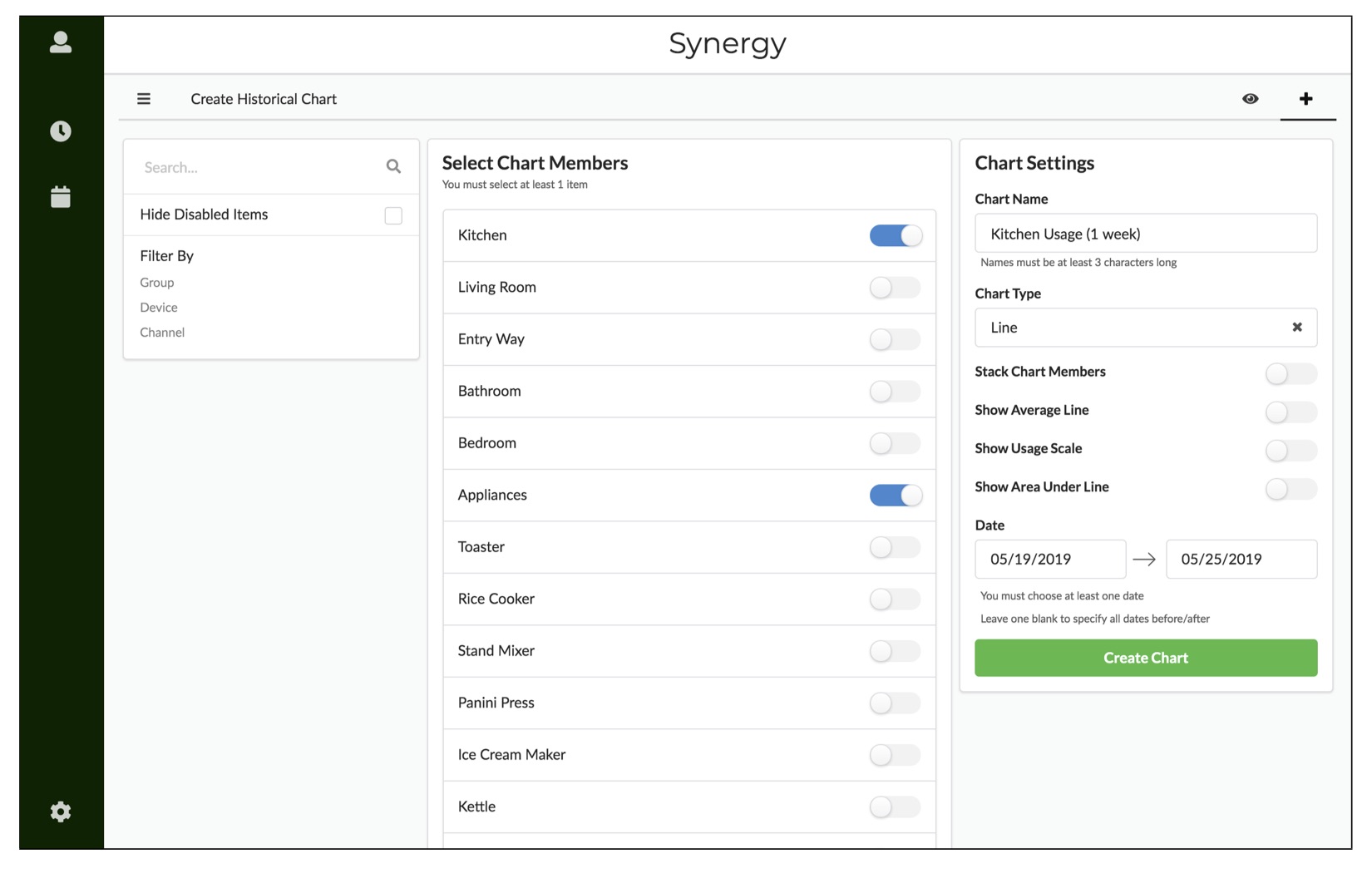
Synergy: An Energy Monitoring and Visualization System
Sarah Johnson, Pearce Ropion
The key to becoming a more sustainable society is first learning to take responsibility for the role we play in energy consumption. Real-time energy usage gives energy consumers a sense of responsibility over what they can do to accomplish a much larger goal for the planet, and practically speaking, what they can do to lower the cost to their wallets. Synergy is an energy monitoring and visualization system that enables users to gather information about the energy consumption in a building – small or large – and display that data for the user in real-time. The gathered energy usage data is processed on the edge before being stored in the cloud. The two main benefits of edge processing are issuing electricity hazard warnings immediately and preserving user privacy. In addition to being a scalable solution that intended for use in individual households, commercial offices and city power grids, Synergy is open-source so that it can be implemented more widely. This paper contains a system overview as well as initial finding based on the data collected by Synergy before assessing the impact the system can have on society.
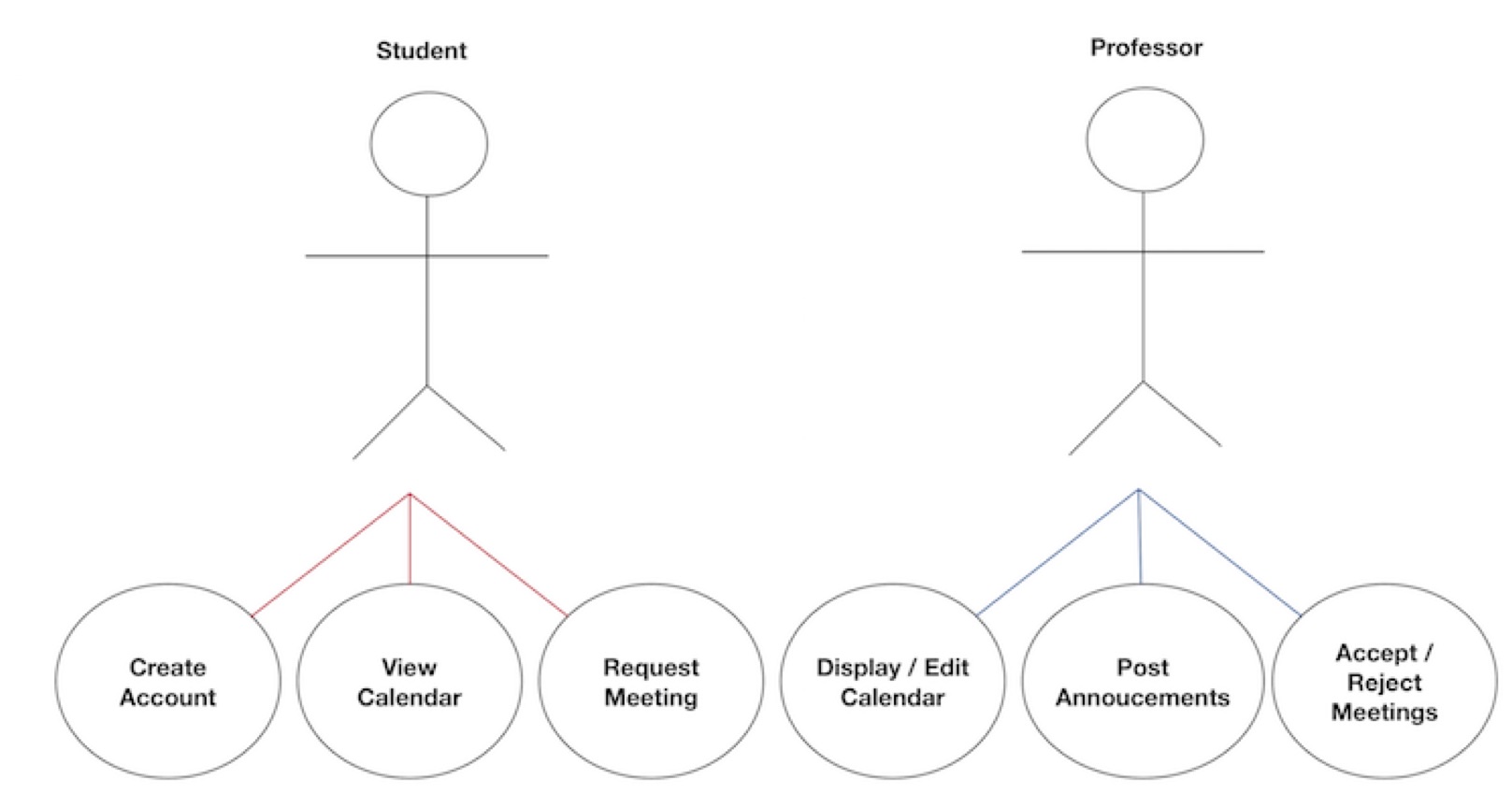
Smart Office Assistant for University Professors
Ben Brown, Francesco Petrini, Alfredo Sepulveda
We present an efficient multipurpose system to enable professors to help students meet with them outside of class. Currently, should a student wish to schedule a meeting with a professor, they often have to initiate a long string of emails until a final date and time can be agreed upon. Additionally, professors have no way to broadcast messages to people visiting their office or take messages from those individuals should a professor be absent. Our solution aims to fix these issues through the use of several low-power, budget-friendly devices. Our platform includes a touchscreen powered by a Raspberry Pi 3, which displays the professor’s public calendar and announcements. Additionally, a camera is used to perform face recognition to map students to the accounts they create to interface with the system. Finally, we created a mobile app that will allow students and professors to communicate quickly in a way that abstracts their phone numbers.
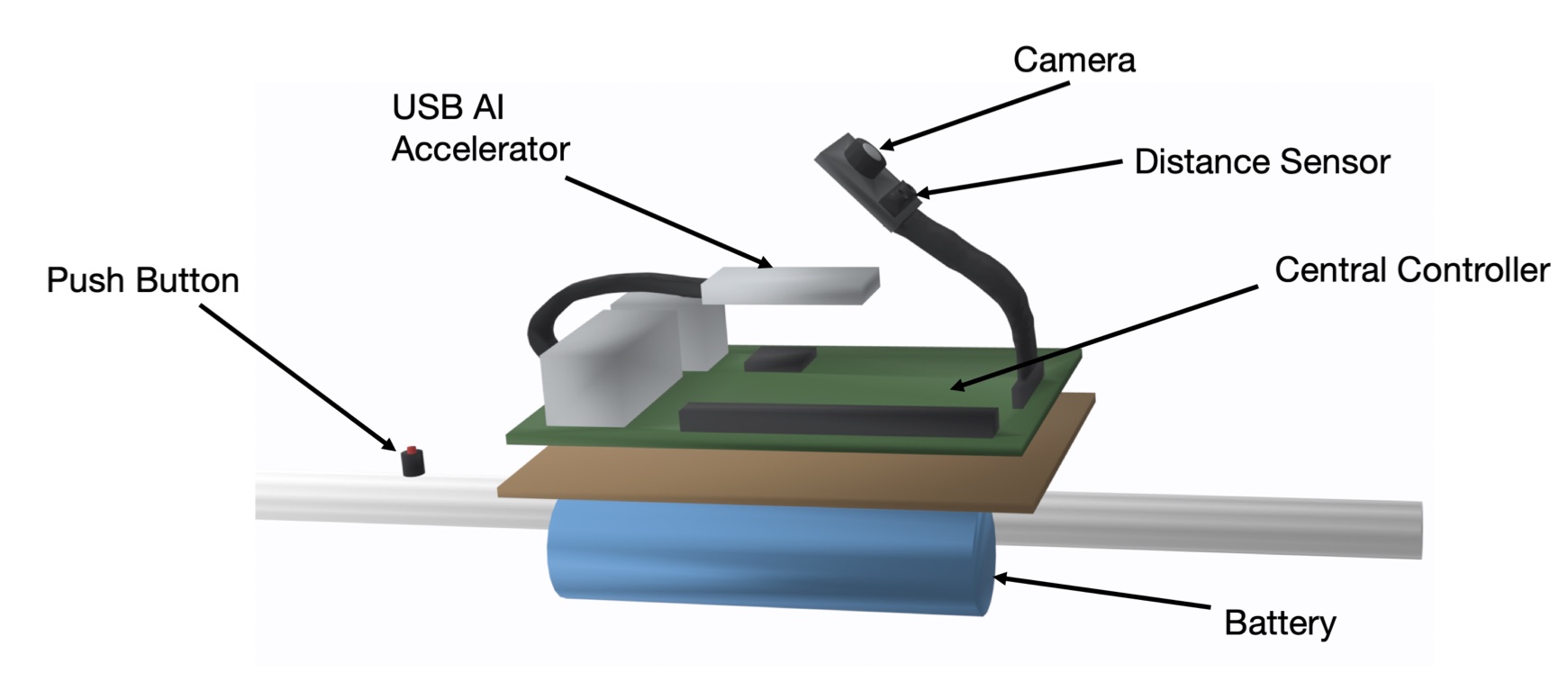
NavSense: A Navigation Tool for Visually Impaired
John Ryan, Daniel Okazaki, Michael Dallow
The visually impaired rely heavily on hearing and touching (with their cane) to navigate through life. These senses cannot make up for vision loss when identifying objects in the user's path. This project proposes NavSense, an assistive device that supplements existing technology to improve navigation and peace of mind in day-to-day life. NavSense provides real-time object identification and context to the user through auditory feedback. The device reduces inference time by 50% without significant power consumption increases. We plan to continue testing on different platforms to improve the device's power consumption further.
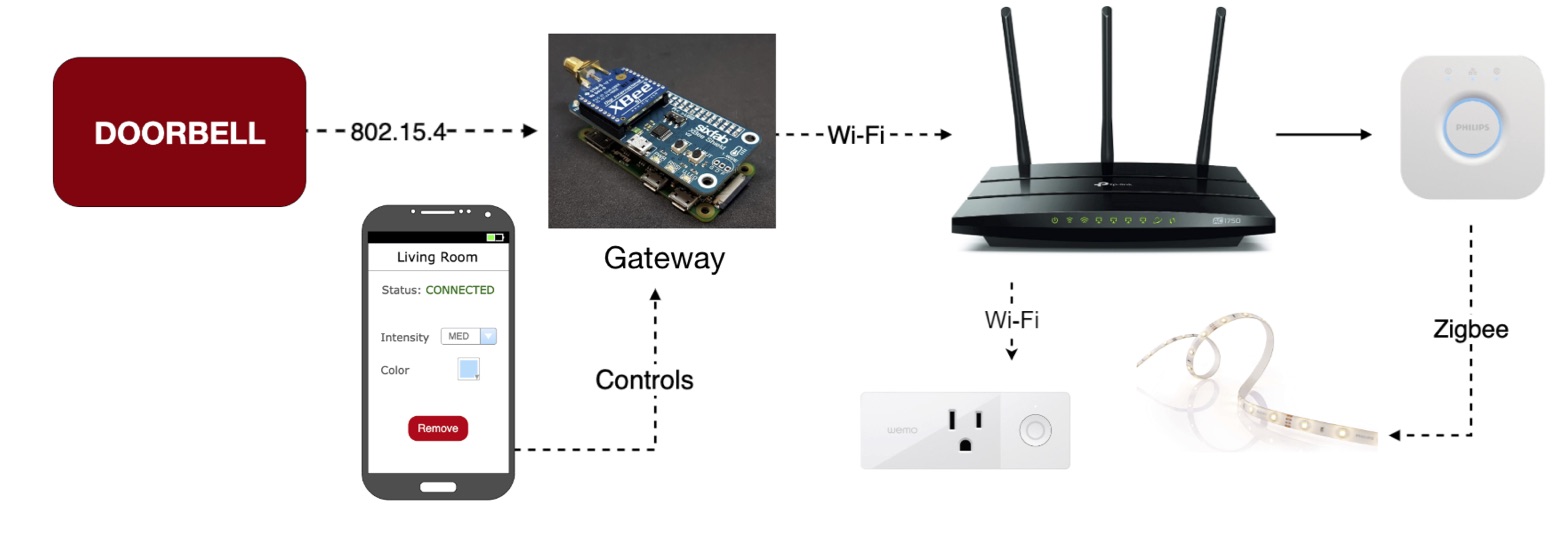
Smart Doorbell System for the Hearing Impaired
Shannen Edwin, Dominic Magdaluyo
Doorbell options for hearing-impaired individuals are seriously limited. Affordable solutions are not scalable, while other solutions are expensive. With this in mind, we designed a scalable and affordable system that will benefit hearing-impaired individuals by informing them regarding doorbells. Due to the scope of the project, we only designed a proof of concept, hoping that a company can create a viable product that will benefit hearing-impaired individuals and bring a powerful IoT system to the homes of others.
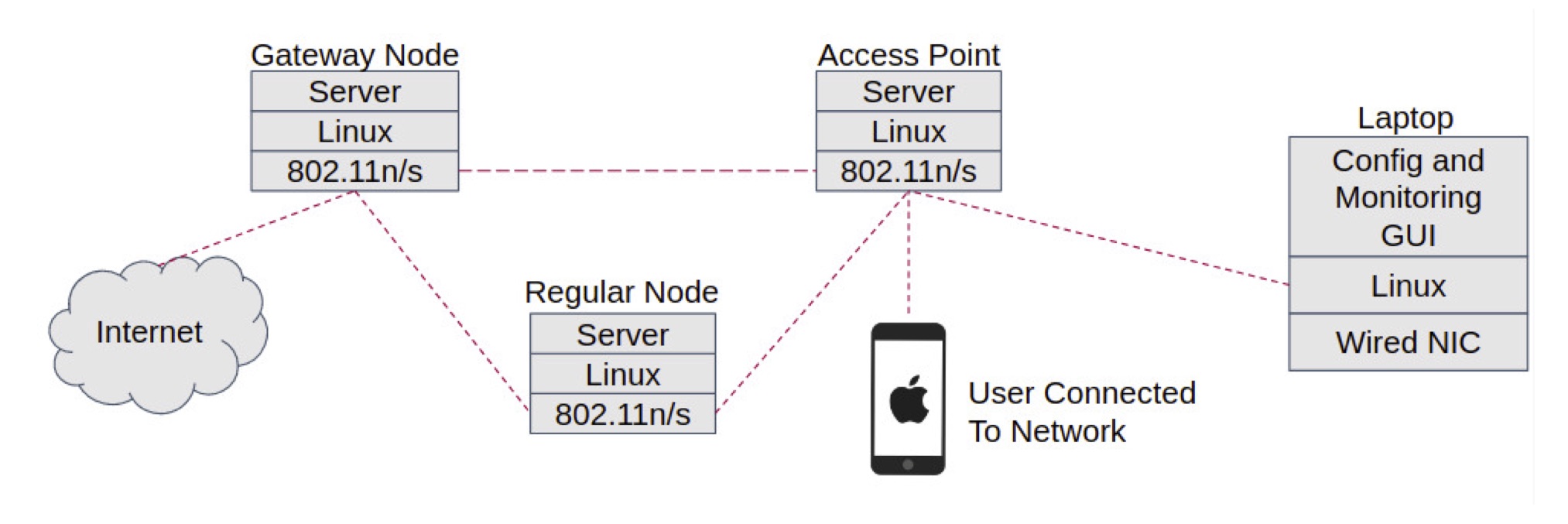
Top Level Mesh
Tristen Islam, Matt Jasaitis
We have built a web-based system for mesh network management. This system allows network utilities to be used from a web-based interface to monitor and manage data transfer. The system runs primarily on Raspberry Pis using Raspbian Linux. Users can access the system through web browsers to configure the system and interact with the data on the network. We discuss our motivation for the project, design decisions made, technologies used, and more throughout this report. We conclude with some lessons learned and future work to be done.
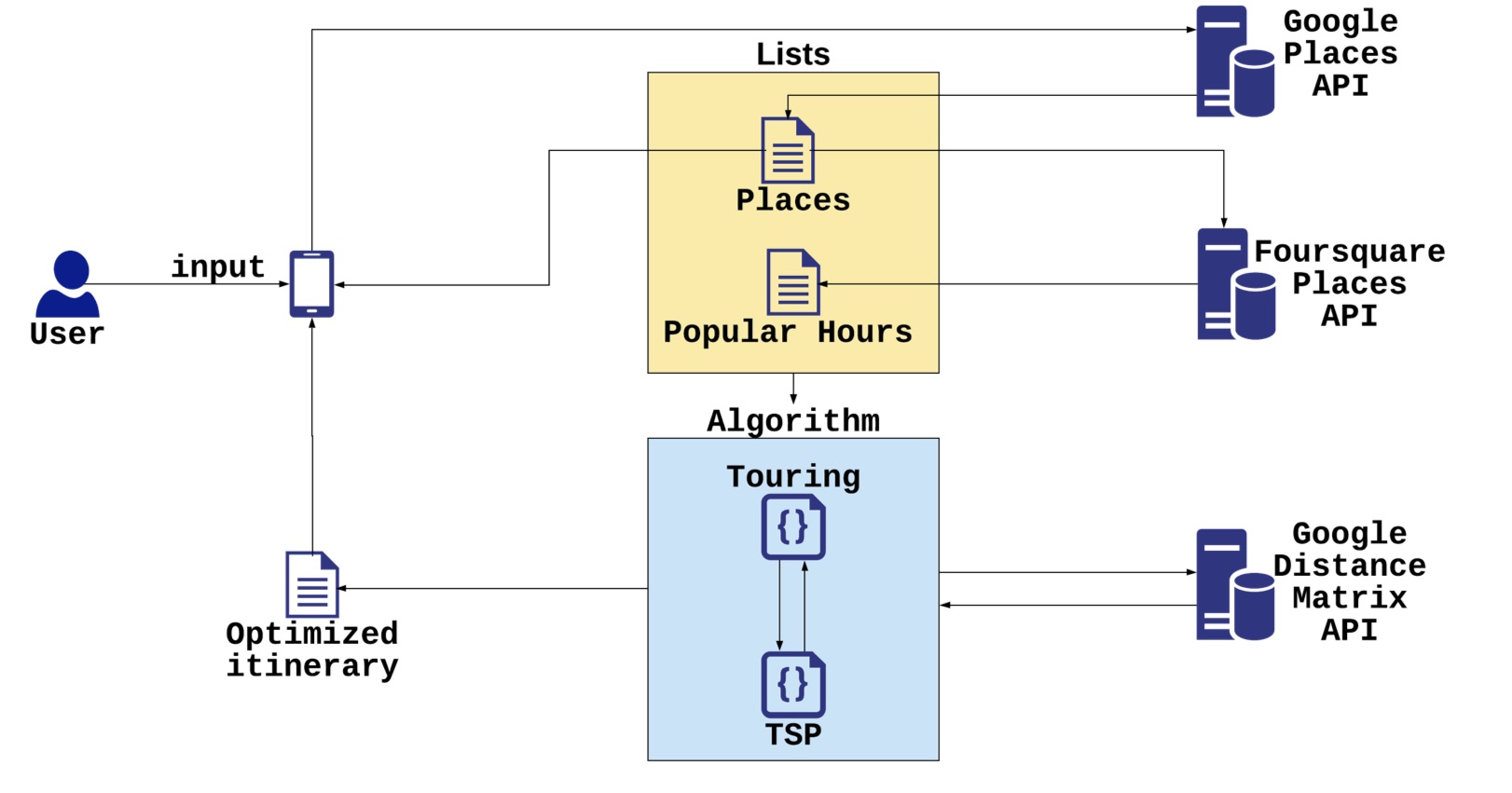
TrippIt: Optimal Itinerary Generator
Andrew Nguyen, Osama Shoubber
Travelers often lose interest and joy when traveling in tourist-packed areas around the world. As more restaurants and attractions open up in popular cities, the wait and travel time from one location to another inevitably increases. Each attraction has certain hours throughout the day where visitors surge and the wait times increase. In addition, traffic and travel time are important factors to consider when looking to optimize one's trip. However, it isn't easy to calculate and consider the most optimal routes and times an individual should visit each possible attraction with large attractions. Travelers ultimately face an issue with maximizing productivity for their trips. Our goal is to create a mobile application that utilizes the Google Directions API and Foursquare API data to produce an optimal itinerary for travelers to use. Travelers will be able to input their place of stay, attractions they want to visit at their preferred times, and other time constraints to produce an itinerary that will allow the tourist to visit each attraction they please. The Optimal Itinerary Generator will eliminate blind spots in travel planning and, as a result, make vacation trips more time efficient and enjoyable.
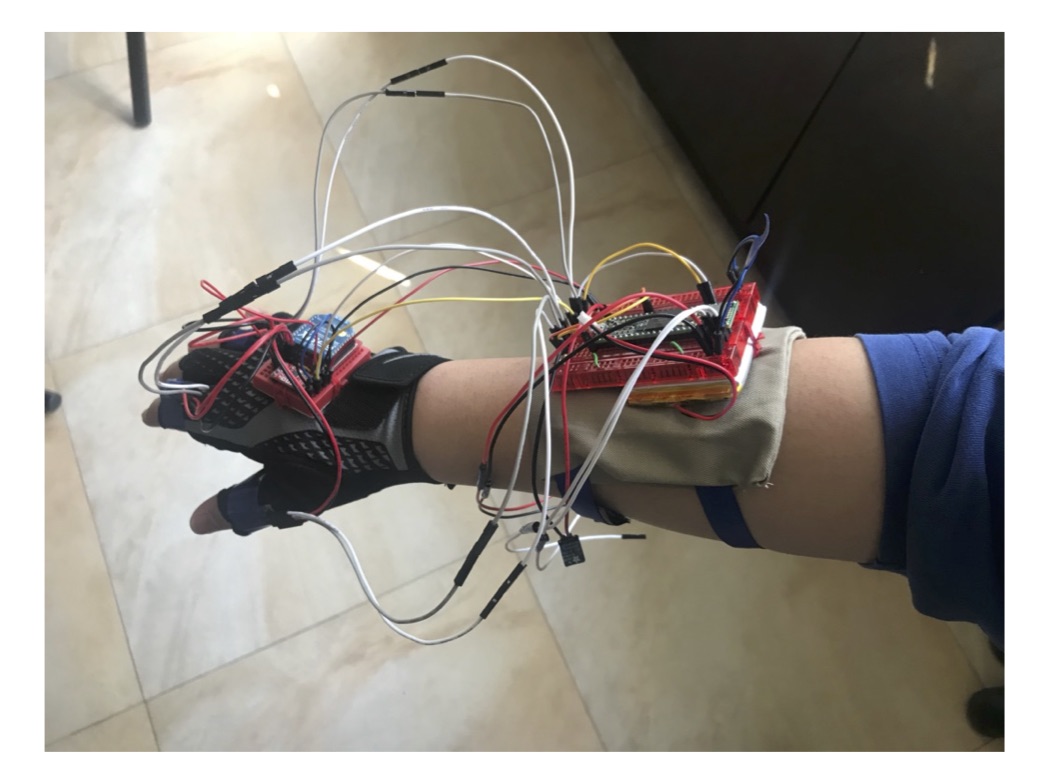
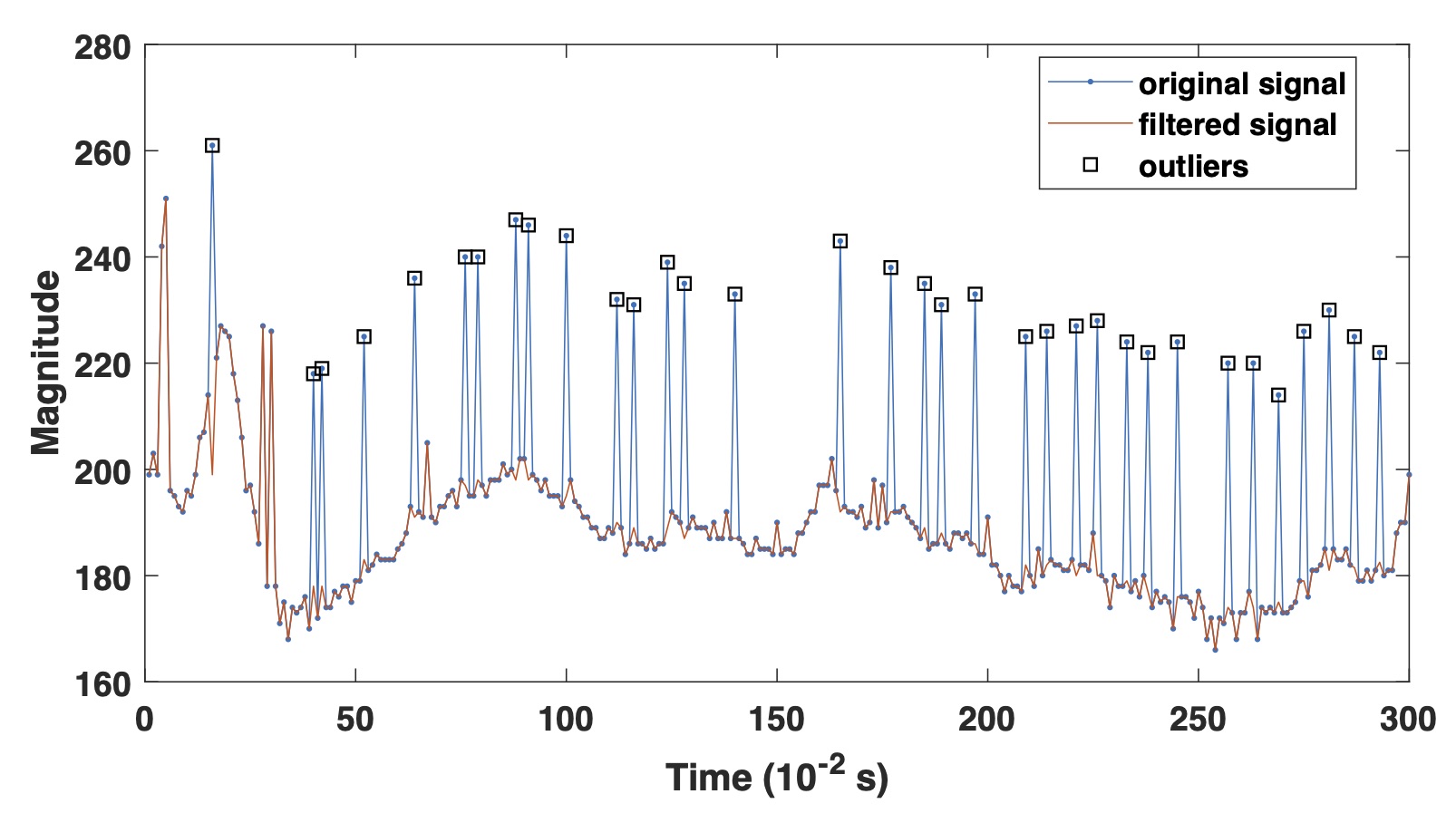
Low-Cost and Energy-Efficient Platform forUnsupervised Parkinson’s Disease Assessmen
Alexander Adranly, Senbao Lu, Yousef Zoumot
Parkinson's Disease (PD) is a progressive neurological disease that affects 6.2 million people worldwide. The most prevalent clinical method to measure PD tremor severity is a standardized test called the Unified Parkinson's Disease Rating Scale (UPDRS), performed subjectively by a medical professional. Due to infrequent checkups and the human error introduced into the process, treatment is not optimally adjusted for PD patients. According to a recent review, there are two devices recommended to quantify PD symptom severity objectively. Both devices record a patient's tremors using inertial measurement units (IMUs). One is not currently available for over-the-counter purchases, as they are currently undergoing clinical trials. It has also been used in studies to evaluate UPDRS scoring in home environments using an Android application to drive the tests. The other device is an accessible product used by researchers to design home monitoring systems for PD tremors at home. Unfortunately, this product includes only the sensor and requires technical expertise and resources to set up the system. This project proposes a low-cost and energy-efficient hybrid system that monitors a patient's daily actions to quantify hand and finger tremors based on relevant UPDRS tests using IMUs and surface Electromyography (sEMG). This device can operate in a home or hospital environment and reduces the cost of evaluating UPDRS scores from patients' and clinicians' perspectives. The system consists of a wearable device that collects data and wirelessly communicates with a local server that performs data analysis. The system does not require any choreographed actions, so that there is no need for the user to follow any unwieldy peripheral. To avoid frequent battery replacement, we employ low-power wireless technology and optimize the software for energy efficiency. Each collected signal is filtered for motion classification, where the system determines the analysis methods best fit each period of signals. The corresponding UPDRS algorithms are then used to analyze the signals and give a score to the patient. We explore six different machine learning algorithms to classify a patient's actions into appropriate UPDRS tests. To verify the platform's usability, we conducted several tests. We measured the accuracy of our main sensors by comparing them with a medically approved industry device. Our device and the industry device show similar measurements with errors acceptable for the significant difference in cost. We tested the lifetime of the device to be 15.16 hours minimum assuming the device is constantly on. Our filters work reliably, demonstrating a high level of similarity to the expected data. Finally, the device is run through an end-to-end sequence, where we show that the platform can collect data and produce a score estimate for the medical professionals.
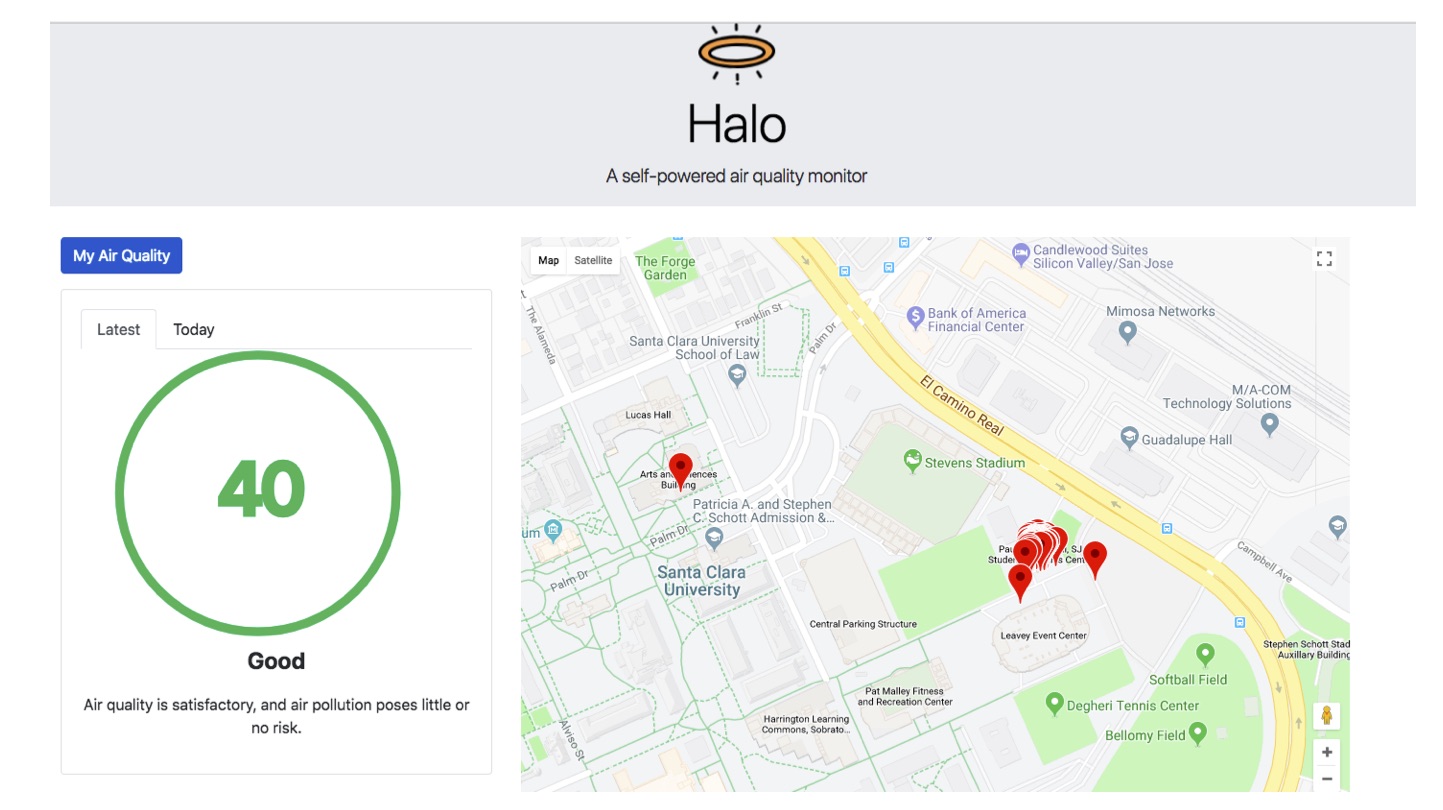
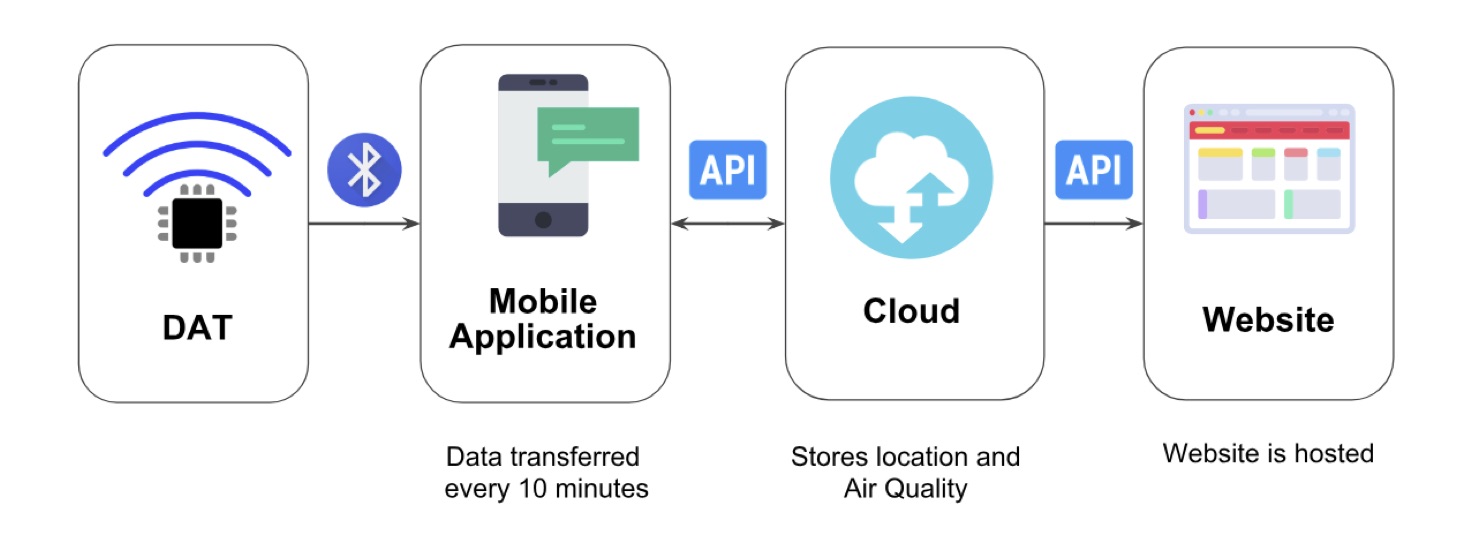
Halo: A Portable and Low-Power Air Quality Monitor
Benjamin Lampe, Taylor Mau, Samantha Morehead, Naeem Turner-Bandele
Urban air pollution leads to widespread respiratory illness and millions of deaths annually. PM2.5, particulate matter with a diameter less than 2.5 micrometers, is the product of many common combustion reactions and poses a severe health risk. Its small size allows it to penetrate deep into the lungs and enter the bloodstream. Existing air quality monitors are aimed at scientific research, differentiating between pollutants, and providing high measurement accuracy. These devices are prohibitively expensive and cannot easily be carried around. Due to the highly localized nature of air pollution and to allow individuals and institutions to monitor their real-time exposure to PM2.5 easily, we propose Halo, an air quality monitor costing less than $100. Halo is powered by a 500 mW solar panel and equipped with a 1500 mAh Lithium-Ion battery to handle 150 mW peak power consumption and operate continuously for over 24 hours without power input. The device is small enough to be clipped to a backpack or bag for easy portability, and it can be used in personal or public settings. Using an IR emitter and detector, Halo measures reflected IR light to determine the particulate concentration in the air with an error of less than 10%. It uses Bluetooth Low Energy (BLE) to communicate these values to a user’s phone. From the phone, air data can be time-stamped, stored in a cloud database, and visualized in an app for easy monitoring of pollution trends and pollution exposure. Additionally, the cloud database allows for aggregating data from multiple devices to create crowdsourced pollution maps. These maps can pinpoint areas with awful air quality to try to make changes to these areas or help users avoid these areas if possible.
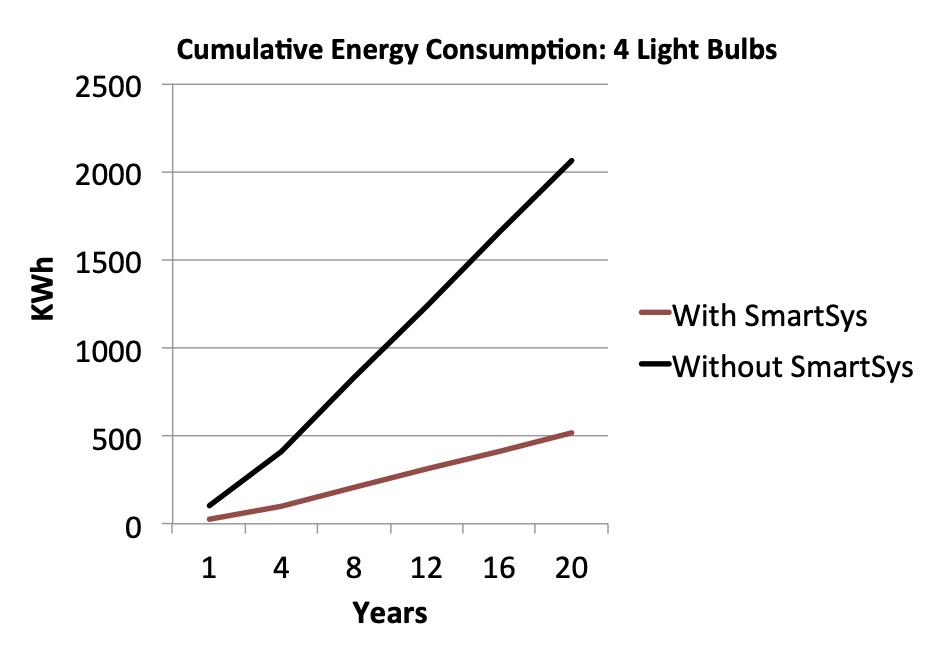
Energy Conservation of Buildings using IoT Devices
Jun Chang, Darence Lim, Tracy Sun
Buildings such as apartment complexes and high-rises consume large amounts of energy, with commercial buildings wasting, on average, 30% of the energy that they consume. This issue leads to drastic consequences such as an increase in carbon footprint and high energy costs. We create a solution that decreases energy consumption and cost. Our project achieves this goal with a scalable and personalized smart home system that caters to individual users’ needs while conserving energy on a large scale. Our solution, SmartSys, cuts energy consumption and energy costs through interaction with IoT devices, an architecture that includes a combination of database-centric and event-driven data flows, and various technologies, including sensors and machine learning. As a result of single room testing, we estimate that SmartSys will help individual users save over $1000 over 20 years and save a city with 20 apartment complexes over 150 million kWh after 20 years. For future work, we hope to decrease the fixed cost of SmartSys to make our solution have an even more significant impact on energy cost savings while maintaining its energy-saving performance. In addition, we hope to engage in multiple room testing and scale SmartSys to function throughout a large building.
Copyright 2024 | Behnam Dezfouli